access control card programming Facility Code – also sometimes called “Site Code”, this is part of the internal programming that is common to all cards on an order. Your organization may or may . See more Using the integrated RFID antenna, NEO 2 can read 98% of commercially available RFID transponders in the HF/NFC as well as in the LF range. It supports HF transponders of the ISO standards ISO/IEC 14443A/B, ISO 15693 and ISO .
0 · wireless access control card readers
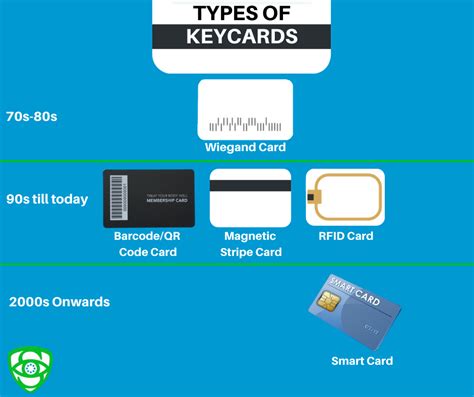
1 · types of access control cards
2 · card access control systems companies
3 · best key card access systems
4 · access control proximity cards
5 · access control card printers
6 · access control card calculator
7 · access card issuance daily monitoring
NFC tag reader is an NFC device that works in NFC reader or writer mode, which enables this NFC device to read information stored on inexpensive NFC tags embedded in labels or smart posters. To make the NFC .
HID manufacturers a number of credential formats. The type of HID credential you use will depend on your access control system. So your first step in finding the right credential is to check your HID System, which should specify the correct prox format. HID assigns a Format code to each Prox Card that indicates how . See moreAfter determining the correct base part number, choose your programming specifications. Each HID prox card not only includes the base part number, but also a . See more
Facility Code – also sometimes called “Site Code”, this is part of the internal programming that is common to all cards on an order. Your organization may or may . See moreFor this sample order of an HID Prox Card 1326, the card appearance options (LGSMV) break down as follows: L = Programmed, Low Frequency (125 kHz) . See more
Learn about the process of ordering your door access cards (also called "proximity" cards) and .Proximity cards, also known as Prox cards or access control cards, are contactless ID cards or keyfobs containing programming that is “read” by a card reader to control and secure physical access.
Learn about the process of ordering your door access cards (also called "proximity" cards) and how to get them programmed. Get details at IDWholesaler.com. In this article we will explain the types of access control cards and how to identify HID® card types and programming information for re-ordering correctly. In addition to that we will briefly cover the basics of door access control systems and how access cards and fobs work.
In an RFID access control system, each RFID card has a unique identifier (UID) that can be used to distinguish one card from another. In this particular Arduino project, the UID of the card is checked to grant or deny access. . Pauses the program for 3 seconds to allow the message to be read. lcd.clear(): Clears the LCD display.
All HID key fob or card come with a format code that basically specifies how the card will communicate with the access control reader and how it is programmed. Finding this can help determine which cards to get. Proximity cards, also known as prox cards or access control cards, are contactless ID cards created with a technology that is read by a card reader to control access to a building. They are an excellent option for offices looking to enhance workplace security and limit the number of unauthorized entries. Due to its durability, a proximity card . In this guide, we will walk you through the basics of RFID technology, explain how an RFID card works, and provide step-by-step instructions on programming RFID cards. You don’t need to have any prior programming experience, as we will cover everything you need to know in a beginner-friendly manner. What does it mean to program an access control card? In simple terms, programming an access control card means adding information to the chip inside a card. This information is the credential data used to communicate with access control card readers, to grant users access to the building.
The 734 Access Control Module allows you to use the powerful, built-in access control capability of DMP Panels using smartcard, proximity, mag stripe, or biometric readers and other compatible authentication devices.

what is dell smart card reader
wireless access control card readers
My question is regarding PAC (personal access control), more specifically programming a card. I am not trying to create any applications or interfaces, rather just putting the basic required data into a "blank" DESFire card using the wiegand format.Proximity cards, also known as Prox cards or access control cards, are contactless ID cards or keyfobs containing programming that is “read” by a card reader to control and secure physical access.
Learn about the process of ordering your door access cards (also called "proximity" cards) and how to get them programmed. Get details at IDWholesaler.com. In this article we will explain the types of access control cards and how to identify HID® card types and programming information for re-ordering correctly. In addition to that we will briefly cover the basics of door access control systems and how access cards and fobs work. In an RFID access control system, each RFID card has a unique identifier (UID) that can be used to distinguish one card from another. In this particular Arduino project, the UID of the card is checked to grant or deny access. . Pauses the program for 3 seconds to allow the message to be read. lcd.clear(): Clears the LCD display.
All HID key fob or card come with a format code that basically specifies how the card will communicate with the access control reader and how it is programmed. Finding this can help determine which cards to get.
Proximity cards, also known as prox cards or access control cards, are contactless ID cards created with a technology that is read by a card reader to control access to a building. They are an excellent option for offices looking to enhance workplace security and limit the number of unauthorized entries. Due to its durability, a proximity card . In this guide, we will walk you through the basics of RFID technology, explain how an RFID card works, and provide step-by-step instructions on programming RFID cards. You don’t need to have any prior programming experience, as we will cover everything you need to know in a beginner-friendly manner. What does it mean to program an access control card? In simple terms, programming an access control card means adding information to the chip inside a card. This information is the credential data used to communicate with access control card readers, to grant users access to the building.
The 734 Access Control Module allows you to use the powerful, built-in access control capability of DMP Panels using smartcard, proximity, mag stripe, or biometric readers and other compatible authentication devices.
types of access control cards
utrust 2700 r contact smart card reader

NOTE: there are 2 readers in the AMS between 1&2, and 3&4, you want the NFC sticker to be .
access control card programming|types of access control cards