access control card policy The purpose of the key and access control card policy and procedure document is twofold, 1) to establish clear guidelines to personnel for requesting, distributing, retrieving and de-activating keys and access cards to a wide variety of people on the Griffin Campus, and 2) to maintain accountability to the inventory of distributed keys and . Smart Card Emulator. Use your phone as contact-less smart card. The Android Smart Card Emulator allows the emulation of a contact-less smart. card. The emulator uses Android's HCE to fetch process APDUs from a NFC .
0 · wireless access control card readers
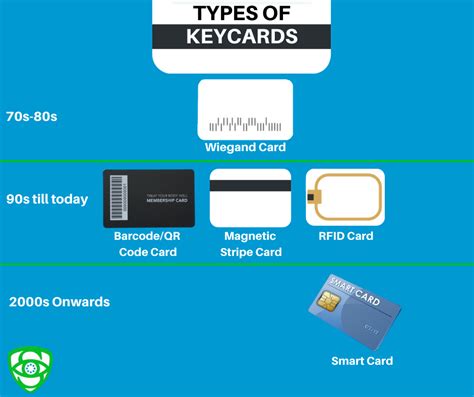
1 · types of access control cards
2 · card access control systems companies
3 · best key card access systems
4 · access control proximity cards
5 · access control card printers
6 · access control card calculator
7 · access card issuance daily monitoring
Clone NFC tags to another tag or to your phone. Keep your cards in one app! Wallet Agent is .
It is the policy of the University of Delaware to issue building and room keys/access cards to faculty, staff, resident students, authorized non-resident students, and persons or organizations with contractual agreements with the University.The purpose of the key and access control card policy and procedure document is twofold, 1) .
It is the policy of the University of Delaware to issue building and room keys/access cards to faculty, staff, resident students, authorized non-resident students, and persons or organizations with contractual agreements with the University.The purpose of the key and access control card policy and procedure document is twofold, 1) to establish clear guidelines to personnel for requesting, distributing, retrieving and de-activating keys and access cards to a wide variety of people on the Griffin Campus, and 2) to maintain accountability to the inventory of distributed keys and .This policy covers all university facilities; all keys, cards, and other devices that control access to university facilities; and all individuals granted access permission to university facilities.
Access cards are issued to State employees and contractors requiring after-hours access, access to facilities that are locked 24/7, or access to certain gated parking areas. Personnel not requiring an access card for access will instead be issued a photo ID card. Organizations planning to implement an access control system should consider three abstractions: access control policies, models, and mechanisms. Access control policies are high-level requirements that specify how access is managed and who may access information under what circumstances. The purpose of this Policy is to regulate access to University property and to ensure that any individual, college, department, operating unit or program, within the scope of this Policy, is aware of their respective responsibilities when assigned CatCards and building keys.The ultimate guide includes an ISO 27001 Access Control Policy Template, Access Control Policy Example and ISO 27001 certification guide.
PURPOSE OF THIS POLICY. To enhance security in its buildings, Lehigh University controls access to all buildings by limiting and controlling the use and function of both access cards and keys issued to all faculty, staff, students, contractors, outside vendors, as well as conference and camp participants. AUTHORITY FOR THIS POLICY.Access controls protect network resources against unauthorized access. Learn how to create an effective access control policy that meets your security needs.
This policy should ensure effective key/card access to provide security for our buildings and for the personnel housed or working in these buildings and property. DEFINITIONS A Aporover: The authorizer is the approved next level supervisor who has the authority to grant keycard access to an individual requesting key/card access.It is the policy of the University of Delaware to issue building and room keys/access cards to faculty, staff, resident students, authorized non-resident students, and persons or organizations with contractual agreements with the University.The purpose of the key and access control card policy and procedure document is twofold, 1) to establish clear guidelines to personnel for requesting, distributing, retrieving and de-activating keys and access cards to a wide variety of people on the Griffin Campus, and 2) to maintain accountability to the inventory of distributed keys and .
This policy covers all university facilities; all keys, cards, and other devices that control access to university facilities; and all individuals granted access permission to university facilities.Access cards are issued to State employees and contractors requiring after-hours access, access to facilities that are locked 24/7, or access to certain gated parking areas. Personnel not requiring an access card for access will instead be issued a photo ID card.

Organizations planning to implement an access control system should consider three abstractions: access control policies, models, and mechanisms. Access control policies are high-level requirements that specify how access is managed and who may access information under what circumstances. The purpose of this Policy is to regulate access to University property and to ensure that any individual, college, department, operating unit or program, within the scope of this Policy, is aware of their respective responsibilities when assigned CatCards and building keys.The ultimate guide includes an ISO 27001 Access Control Policy Template, Access Control Policy Example and ISO 27001 certification guide.
wireless access control card readers
PURPOSE OF THIS POLICY. To enhance security in its buildings, Lehigh University controls access to all buildings by limiting and controlling the use and function of both access cards and keys issued to all faculty, staff, students, contractors, outside vendors, as well as conference and camp participants. AUTHORITY FOR THIS POLICY.Access controls protect network resources against unauthorized access. Learn how to create an effective access control policy that meets your security needs.
chicago bears standings 2022
types of access control cards
card access control systems companies
This video explains how to program an NFC business card using NFC tools which is a free app on the Apple and Android store. I walk you through step by step o.
access control card policy|best key card access systems