data backup smart card security Liu et al. (IET Information Security 2017) designed a data backup scheme using secret sharing scheme and mutual authentication scheme. They divided the key into three parts and stored them in the laptop, smart card and server respectively.
The Kick Six (also known as Kick Bama Kick) was the final play of the 78th Iron Bowl college football game played on November 30, 2013, at Jordan–Hare Stadium in Auburn, Alabama. The game featured the No. 1-ranked and two-time defending national champion Alabama Crimson Tide (11–0, 7–0 in the SEC) as a 10-point favorite over the No. 4-ranked Auburn Tigers (10–1, 6–1 in the SEC). T.
0 · Enhanced secure data backup scheme using multi‐factor
1 · Enhanced secure data backup scheme
2 · Data Backups: Its Importance for Cybers
3 · An Improved Data Backup Scheme Bas
4 · A secure data backup scheme using multi
5 · A secure data backup scheme using mu
They worked in BotW, and I just confirmed my Loftwing NFC chip works. Got the goddess fabric! Yes. Amiibos are just plastic toys with chips inside. You can .
Enhanced secure data backup scheme using multi‐factor
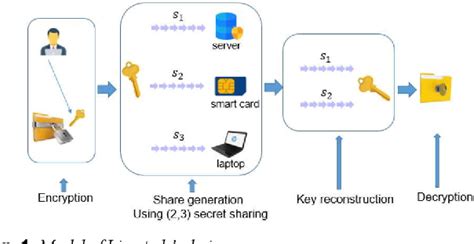
A user-centred design data backup scheme is proposed using multi-factor authentication. The user firstly selects a symmetrical key and divides it into three shares, then destroys the key. The key can easily be reconstructed by combining the shares stored in the . They present an enhanced secure data backup scheme using multi-factor .
rfid tracking system pdf
A user-centred design data backup scheme is proposed using multi-factor authentication. The user firstly selects a symmetrical key and divides it into three shares, then destroys the key. The key can easily be reconstructed by combining the shares stored in the user's smart card and the laptop. They present an enhanced secure data backup scheme using multi-factor authentication to overcome all above-mentioned security threats. The user first divided a secret used to encrypt sensitive data into three shares using Shamir's secret sharing. Remote data backup technology facilitates data storage for users. However, an attacker may intercept some sensitive data on transfer. To solve this problem, sensitive data should be encrypted before uploading to the remote storage. Thus, protecting the secret encryption key is very important.
Liu et al. (IET Information Security 2017) designed a data backup scheme using secret sharing scheme and mutual authentication scheme. They divided the key into three parts and stored them in the laptop, smart card and server respectively. The goal of the backup is to deposit your data to a separate, secure location away from your devices where it can be retrieved when necessary. Using a 3-2-1 backup strategy increases the likelihood that your data has been properly duplicated, and .
You can back up your data with an online backup service by encrypting your files, scheduling regular backups, and storing the backup files in a safe location. Online backup services are a great way to protect your data in case of a computer crash or theft. The experts we spoke with recommended enrolling a second security key as a backup, and they warned that enabling different forms of MFA for one account makes you vulnerable to phishing. From password managers to backup software, here are the apps and services everyone needs to protect themselves from security breaches and data loss.
Inspired by these excellent works, a more robust data backup scheme is proposed, in which the key is selected by the user, and be destroyed to avoid the key leakage as soon as it is divided into three shares. Normally, the user retrieves the key with the registered laptop and the smart card. TechTarget's data backup guide discusses the importance of backup, outlines the benefits and challenges of providing this layer of data protection and provides an overview of different backup approaches, technologies and vendors. A user-centred design data backup scheme is proposed using multi-factor authentication. The user firstly selects a symmetrical key and divides it into three shares, then destroys the key. The key can easily be reconstructed by combining the shares stored in the user's smart card and the laptop. They present an enhanced secure data backup scheme using multi-factor authentication to overcome all above-mentioned security threats. The user first divided a secret used to encrypt sensitive data into three shares using Shamir's secret sharing.
Remote data backup technology facilitates data storage for users. However, an attacker may intercept some sensitive data on transfer. To solve this problem, sensitive data should be encrypted before uploading to the remote storage. Thus, protecting the secret encryption key is very important.Liu et al. (IET Information Security 2017) designed a data backup scheme using secret sharing scheme and mutual authentication scheme. They divided the key into three parts and stored them in the laptop, smart card and server respectively. The goal of the backup is to deposit your data to a separate, secure location away from your devices where it can be retrieved when necessary. Using a 3-2-1 backup strategy increases the likelihood that your data has been properly duplicated, and . You can back up your data with an online backup service by encrypting your files, scheduling regular backups, and storing the backup files in a safe location. Online backup services are a great way to protect your data in case of a computer crash or theft.
The experts we spoke with recommended enrolling a second security key as a backup, and they warned that enabling different forms of MFA for one account makes you vulnerable to phishing. From password managers to backup software, here are the apps and services everyone needs to protect themselves from security breaches and data loss.Inspired by these excellent works, a more robust data backup scheme is proposed, in which the key is selected by the user, and be destroyed to avoid the key leakage as soon as it is divided into three shares. Normally, the user retrieves the key with the registered laptop and the smart card.
Enhanced secure data backup scheme
Data Backups: Its Importance for Cybers
running rfid systems
An Improved Data Backup Scheme Bas
TuneIn. Listen to Auburn Football on TuneIn. Plus, fuel your fandom with local and national sports talk, pregame and postgame analysis, all your favorite sports podcasts, and live coverage of .
data backup smart card security|Enhanced secure data backup scheme using multi‐factor