authentication method required for the use of smart cards Smart cards can be used to sign in to domain accounts only, not local accounts. When you use a password to sign in interactively to a domain account, Windows uses the Kerberos version 5 (v5) protocol for authentication. NFC, or near-field communication, is a short-range wireless technology that allows your phone to act as a transit pass or credit card, quickly transfer data, or instantly pair with Bluetooth .In this article, we’ll explore each NFC forum tag type and provide examples of NFC cards that belong to these types. NFC Forum Tag Type 1. NFC Forum Tag Type 1 is based on the ISO14443-A standard and is known for its simplicity and flexibility. It’s rewritable and can be .
0 · what is smart card authentication
1 · smart card two factor authentication
2 · smart card certificate authentication
3 · smart card based identification system
4 · smart card authentication step by
5 · smart card authentication process
6 · configure smart card authentication
7 · authenticate using your smart card
Contactless-equipped cards use radio frequency identification (RFID) technology and near-field communication (NFC) to process transactions where possible. Contactless payment is an.
For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers. This topic .
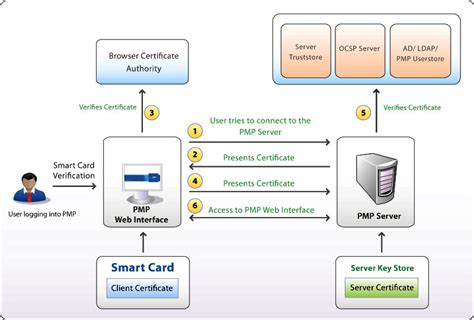
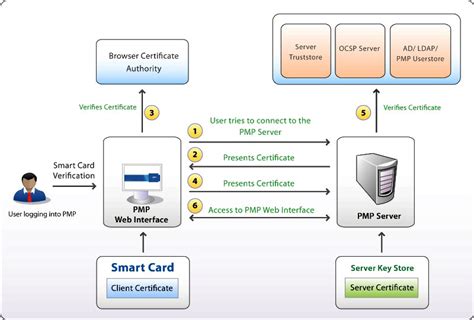
Certificate Requirements and Enumeration: Learn about requirements for smart card certificates based on the operating system, and about the operations that are performed by the operating system when a smart card is inserted into the computer. Smart Card and Remote Desktop Services: Learn about using smart cards for remote desktop connections.For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers. This topic includes information about: Credential provider architecture. Smart card subsystem architecture. Credential provider architecture.
Give smart cards to approved users and help them turn on the cards, choose a secret code, and use the cards properly. Provide classes and help for users to learn about smart card logins and get answers to questions or worries.
Smart cards can be used to sign in to domain accounts only, not local accounts. When you use a password to sign in interactively to a domain account, Windows uses the Kerberos version 5 (v5) protocol for authentication.Use of smart cards for online authentication has been most successful in segments with strong standardization, such as the U.S. government (e.g., the Personal Identity Verification (PIV) card and Common Access Card (CAC)).Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.
Smart card authentication is an important part of cybersecurity, providing an extra layer of protection in our increasingly digital world. It involves the use of smart cards, which are small, pocket-sized cards with embedded integrated circuits or "chips" that can process data. How Smart Card Authentication Works. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.
Authentication: Typically, users prove they are who they say they are by entering a password (something only the user is supposed to know), but to strengthen security, many organizations also require that they prove their identity with something they have (a phone or token device) or something they are (fingerprint or face scan).Certificate Requirements and Enumeration: Learn about requirements for smart card certificates based on the operating system, and about the operations that are performed by the operating system when a smart card is inserted into the computer. Smart Card and Remote Desktop Services: Learn about using smart cards for remote desktop connections.For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers. This topic includes information about: Credential provider architecture. Smart card subsystem architecture. Credential provider architecture. Give smart cards to approved users and help them turn on the cards, choose a secret code, and use the cards properly. Provide classes and help for users to learn about smart card logins and get answers to questions or worries.
Smart cards can be used to sign in to domain accounts only, not local accounts. When you use a password to sign in interactively to a domain account, Windows uses the Kerberos version 5 (v5) protocol for authentication.Use of smart cards for online authentication has been most successful in segments with strong standardization, such as the U.S. government (e.g., the Personal Identity Verification (PIV) card and Common Access Card (CAC)).
what is smart card authentication
Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.Smart card authentication is an important part of cybersecurity, providing an extra layer of protection in our increasingly digital world. It involves the use of smart cards, which are small, pocket-sized cards with embedded integrated circuits or "chips" that can process data. How Smart Card Authentication Works. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.
physical attack smart card
pharmacy smart card canada
smart card two factor authentication

smart card certificate authentication
$37.99
authentication method required for the use of smart cards|smart card based identification system