secure authentication through the use of smart cards Smart card authentication checks who someone is using a smart card. The smart card has a tiny computer chip inside that can securely save and work with information. Smart .
PHP Source code of uFR Online (NFC Reader with wifi, ethernet) example. This examples .
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
This information shows us that a) our Android device has enabled NFC capabilities, b) the NFC chip on the tag (Credit Card) could get read by the devices NFC system and c) — most important .
Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that .How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.
Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that .In this IT area, smart cards enable: Secure login and authentication of users to PCs and networks, Secure B2B and B2C e-commerce, Storage of digital certificates, credentials, and passwords, . Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, .
Smart card authentication checks who someone is using a smart card. The smart card has a tiny computer chip inside that can securely save and work with information. Smart .Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and . Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data .Smart card authentication is an important part of cybersecurity, providing an extra layer of protection in our increasingly digital world. It involves the use of smart cards, which are small, .
Smart cards are tamper-resistant portable storage devices that can enhance the security of tasks such as authenticating clients, signing code, securing e-mail, and signing in .Smart card authentication requires two things: the smart card itself and a pin entered by the user. With smart cards there are two different ways to authenticate yourself into a system, there is .
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that .In this IT area, smart cards enable: Secure login and authentication of users to PCs and networks, Secure B2B and B2C e-commerce, Storage of digital certificates, credentials, and passwords, .
Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, . Smart card authentication checks who someone is using a smart card. The smart card has a tiny computer chip inside that can securely save and work with information. Smart .
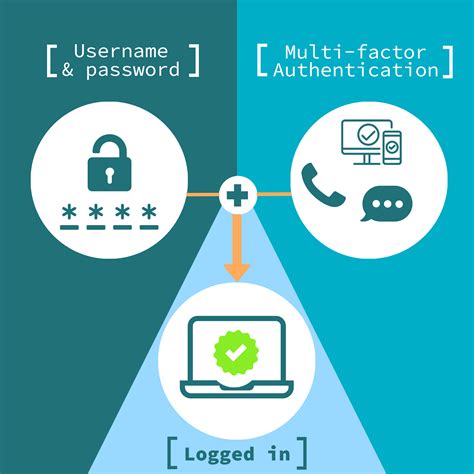
Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and . Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data .Smart card authentication is an important part of cybersecurity, providing an extra layer of protection in our increasingly digital world. It involves the use of smart cards, which are small, .
smart card multi factor authentication
Smart cards are tamper-resistant portable storage devices that can enhance the security of tasks such as authenticating clients, signing code, securing e-mail, and signing in .
destroy rfid tag
smart card identity

smart card based identification system
NFC cards are transforming how businesses manage loyalty programs. These .
secure authentication through the use of smart cards|smart card authentication step by