smart cards tokens security and applications Smart Cards, Tokens, Security and Applications. This book provides a broad overview of the many card systems and solutions that are in practical use today. This new edition adds.
$14.60
0 · what is smart card number
1 · what is smart card authentication
2 · smart card identity
3 · smart card identification
4 · smart card based identification system
5 · smart card based authentication
6 · memory based smart card
7 · azure smart card authentication
Create a playlist and link it to a Yoto card in the normal way (either using your phone or the Yoto player). Insert the MYO card into the Yoto player so that it starts downloading the content. I'd recommend letting your Yoto player .
A step-by-step approach educates the reader in card types, production, operating systems, commercial applications, new technologies, security design, attacks, application development, deployment and lifecycle management. Smart Cards, Tokens, Security and Applications. This book provides a broad . This book combines a cross-discipline overview of smart cards, tokens and . Smart cards, tokens, security and applications. "This book combines a cross .
A step-by-step approach educates the reader in card types, production, operating systems, commercial applications, new technologies, security design, attacks, application development, deployment and lifecycle management. Smart Cards, Tokens, Security and Applications. This book provides a broad overview of the many card systems and solutions that are in practical use today. This new edition adds.
This book combines a cross-discipline overview of smart cards, tokens and related security and applications plus a technical reference to support further research and study. Smart cards, tokens, security and applications. "This book combines a cross-discipline overview of smart cards, tokens, and related security and applications plus a technical reference to support further research and study. A step-by-step approach educates the reader in card types, production, operating systems, commercial applications, new . A step-by-step approach educates the reader in card types, production, operating systems, commercial applications, new technologies, security design, attacks, application development, deployment and lifecycle management. This book combines a cross-discipline overview of smart cards, tokens and related security and applications plus a technical reference to support further research and study.
This new edition adds content on RFIDs, embedded security, attacks and countermeasures, security evaluation, javacards, banking or payment cards, identity cards and passports, mobile systems security, and security management.Smart Cards, Tokens, Security and Applications. Providing a broad overview of the many card systems and solutions in practical use today, this state-of-the art work is written by contributing authors who are active researchers and acknowledged experts in their field. This book offers a broad and useful overview of smart cards technology and applications. In particular, it addresses the RFID technology (for contactless smart card), smart card reader access mechanism, smart card production, multi-application smart card platforms, smart card security and security for pay-TV systems as well as smart card .Smart Cards, Tokens, Security and Applications. This book provides a broad overview of the many card systems and solutions that are in practical use today. This new edition adds content on RFIDs, embedded security, attacks and countermeasures, security evaluation, javacards, banking or payment cards, identity cards and passports, mobile systems .
A step-by-step approach educates the reader in card types, production, operating systems, commercial applications, new technologies, security design, attacks, application development, deployment and lifecycle management.
what is smart card number

what is smart card authentication
Smart Cards, Tokens, Security and Applications. This book provides a broad overview of the many card systems and solutions that are in practical use today. This new edition adds. This book combines a cross-discipline overview of smart cards, tokens and related security and applications plus a technical reference to support further research and study.
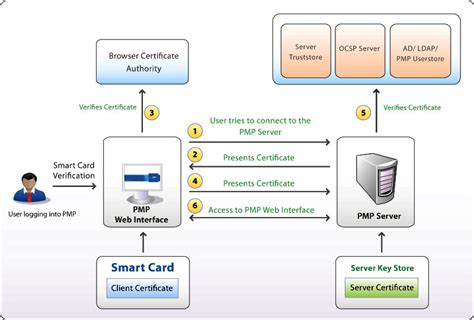
Smart cards, tokens, security and applications. "This book combines a cross-discipline overview of smart cards, tokens, and related security and applications plus a technical reference to support further research and study. A step-by-step approach educates the reader in card types, production, operating systems, commercial applications, new .
A step-by-step approach educates the reader in card types, production, operating systems, commercial applications, new technologies, security design, attacks, application development, deployment and lifecycle management. This book combines a cross-discipline overview of smart cards, tokens and related security and applications plus a technical reference to support further research and study. This new edition adds content on RFIDs, embedded security, attacks and countermeasures, security evaluation, javacards, banking or payment cards, identity cards and passports, mobile systems security, and security management.
Smart Cards, Tokens, Security and Applications. Providing a broad overview of the many card systems and solutions in practical use today, this state-of-the art work is written by contributing authors who are active researchers and acknowledged experts in their field. This book offers a broad and useful overview of smart cards technology and applications. In particular, it addresses the RFID technology (for contactless smart card), smart card reader access mechanism, smart card production, multi-application smart card platforms, smart card security and security for pay-TV systems as well as smart card .

smart card identity

rfid labels growth
The demand for a secure and convenient crypto wallet continues to grow, and NFC wallet cards are quickly gaining popularity as a viable alternative to traditional seed phrase wallets. With the ability to store private keys and perform transactions without the need for . See more
smart cards tokens security and applications|azure smart card authentication