puf korea smart card The UICC smart cards or SIM cards consist of CPU, ROM, SRAM, non-volatile . Explore a wide range of our Zelda Amiibo Nfc Cards selection. Find top brands, exclusive .
0 · what is a puf
1 · puf wikipedia
2 · puf function
3 · puf cryptographic authentication
4 · puf based authentication protocol
Amiibo collectors can fully manage their Amiibo collection in the app. Users can add and update Amiibo data using NFC, delete Amiibo from the collection, search Amiibo to get its details, search Amiibo on Amazon, create personal Wishlist .
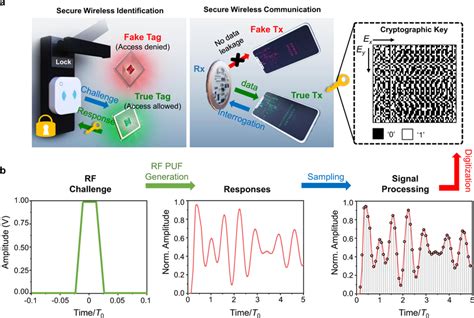
The UICC smart cards or SIM cards consist of CPU, ROM, SRAM, non-volatile . To address the identified vulnerabilities, we present an improved PUF-based .Early references about systems that exploit the physical properties of disordered systems for authentication purposes date back to Bauder in 1983 and Simmons in 1984. Naccache and Frémanteau provided an authentication scheme in 1992 for memory cards. PUFs were first formally proposed in a general fashion by Pappu in 2001, under the name Physical One-Way Function (POWF), with the term PUF being coined in 2002, whilst describing the first integrated .
The UICC smart cards or SIM cards consist of CPU, ROM, SRAM, non-volatile memory like EEPROM, and the ISO/IEC 7816 interface. The USIM cards are intended to securely store the user and the network information within the device.
To address the identified vulnerabilities, we present an improved PUF-based authentication protocol that ensures robust security against all the attacks described in the context of PLAKE and.Starting in 2010, PUF gained attention in the smartcard market as a promising way to provide "silicon fingerprints", creating cryptographic keys that are unique to individual smartcards. [12][13] Explore NXP's on-going efforts in strengthening the security of chips used in smartcards and related embedded authentication technology with PUF.
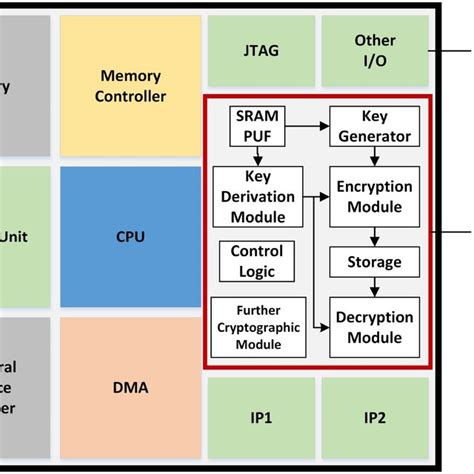
Investigate the definition and capabilities of the cryptographic technology PUF—physically unclonable function. Over the years, PUFs have been widely used in smartcards to provide "silicon fingerprints" as a means of uniquely identifying cardholders based on a challenge-response authentication scheme. The newly proposed method from GIST employs native silk fibers produced by silkworms to create PUF-based tags that are then used to devise a PUF module.ICTK, possessing the world's only 'QPUF-chip' that combines PUF with post-quantum technology, provides various authentication solutions ranging from device-to-network interactions to telecommunications in Korea.In an electronic device, a smart card that directly performs a first part of operations to be performed according to a received request and transmits a command to the PUF chip so that the.
The term “passive PUF” indicates the use of passive components like resistors and capacitors, whereas “active PUF” refers to the use of active components like transistors or SRAM cells. Passive PUFs such as Via PUF provides exceptional .
what is a puf

[Datanet]Identity is the foundation of zero trust, and as we move toward digital transformation and a hyper-connected society, protecting identity becomes a critical challenge. Therefore, the safest way to secure an identity is not to inject it externally, but to make it an inherent characteristic, such as biometric information. This is why 'PUF', also known as 'semiconductor fingerprint', is . The UICC smart cards or SIM cards consist of CPU, ROM, SRAM, non-volatile memory like EEPROM, and the ISO/IEC 7816 interface. The USIM cards are intended to securely store the user and the network information within the device.
update on rfid micro chip
To address the identified vulnerabilities, we present an improved PUF-based authentication protocol that ensures robust security against all the attacks described in the context of PLAKE and.Starting in 2010, PUF gained attention in the smartcard market as a promising way to provide "silicon fingerprints", creating cryptographic keys that are unique to individual smartcards. [12][13] Explore NXP's on-going efforts in strengthening the security of chips used in smartcards and related embedded authentication technology with PUF.
Investigate the definition and capabilities of the cryptographic technology PUF—physically unclonable function. Over the years, PUFs have been widely used in smartcards to provide "silicon fingerprints" as a means of uniquely identifying cardholders based on a challenge-response authentication scheme. The newly proposed method from GIST employs native silk fibers produced by silkworms to create PUF-based tags that are then used to devise a PUF module.ICTK, possessing the world's only 'QPUF-chip' that combines PUF with post-quantum technology, provides various authentication solutions ranging from device-to-network interactions to telecommunications in Korea.
puf wikipedia
In an electronic device, a smart card that directly performs a first part of operations to be performed according to a received request and transmits a command to the PUF chip so that the.The term “passive PUF” indicates the use of passive components like resistors and capacitors, whereas “active PUF” refers to the use of active components like transistors or SRAM cells. Passive PUFs such as Via PUF provides exceptional .

puf function
vaccine with rfid chip
this american life rfid chips
NFC is just a platform for establishing communication between two devices. But NFC's short range, in a sense, serves as a safeguard against hackers. In order to grab an NFC signal from thin air (called eavesdropping), an attacker would .Learn how you can enable or disable NFC and payment on Samsung Galaxy S10 / S10+ / S10e.Android 9 Pie.FOLLOW US ON TWITTER: http://bit.ly/10Glst1LIKE US ON F.
puf korea smart card|puf cryptographic authentication