how to implement smart card authentication Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers. Proxmark 3 RDV4.01 New Accessories; Proxmark 3 "BlueShark" Bluetooth + .
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
To add a PRESTO card to Wallet, you need an iPhone SE (2nd Gen) or iPhone 8 or .
smart card multi factor authentication
Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that meets the secure authentication .
smart card identity
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers.
Smart cards provide an easy and movable way to prove who you are, without needing to remember hard passwords. Smart card security can be combined with other authentication methods like personal identification numbers or biometrics for stronger protection. Implementing Smart Card Authentication: Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.These Windows Domain configuration guides will help you configure your Windows network domain for smart card logon using PIV credentials. There are many useful pages and technical articles available online that include details on configurations and using generic smart cards.
Smart cards are tamper-resistant portable storage devices that can enhance the security of tasks such as authenticating clients, signing code, securing e-mail, and signing in with a Windows domain account.
This document covers the basic steps required to set up an Active Directory domain environment for smart card authentication, including considerations before provisioning YubiKeys for smart card login. Basics of Smart Cards. What is a Smart Card? A smart card is a physical card that contains an embedded integrated circuit or chip. This chip can be either a secure microcontroller or an equivalent intelligent device with internal memory or microprocessor components.
smart card based identification system
smart card authentication step by
long distance rfid reader suppliers
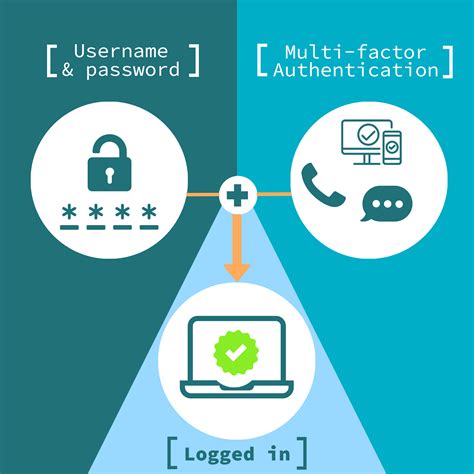
The user flow of smart card authentication is as follows. An employee’s identity is tied to company-deployed smart card, which has an embedded chip that is capable of storing and presenting cryptographic keys.
Implementation practices for using PIV for network authentication (smart card logon) are found under implementations. Who is eligible for a PIV credential?
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers.
Smart cards provide an easy and movable way to prove who you are, without needing to remember hard passwords. Smart card security can be combined with other authentication methods like personal identification numbers or biometrics for stronger protection. Implementing Smart Card Authentication: Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.
These Windows Domain configuration guides will help you configure your Windows network domain for smart card logon using PIV credentials. There are many useful pages and technical articles available online that include details on configurations and using generic smart cards. Smart cards are tamper-resistant portable storage devices that can enhance the security of tasks such as authenticating clients, signing code, securing e-mail, and signing in with a Windows domain account. This document covers the basic steps required to set up an Active Directory domain environment for smart card authentication, including considerations before provisioning YubiKeys for smart card login.
Basics of Smart Cards. What is a Smart Card? A smart card is a physical card that contains an embedded integrated circuit or chip. This chip can be either a secure microcontroller or an equivalent intelligent device with internal memory or microprocessor components.The user flow of smart card authentication is as follows. An employee’s identity is tied to company-deployed smart card, which has an embedded chip that is capable of storing and presenting cryptographic keys.
smart card authentication protocol
enable smart card log on
Method 2: Looking for signs on the card: Some cards may have visible indications indicating the presence of RFID or NFC technology. Look for any logos or symbols on the card that suggest contactless communication. .As with proximity card technology, NFC uses inductive coupling between two nearby loop antennas effectively forming an air-core transformer. Because the distances involved are tiny compared to the wavelength of electromagnetic radiation (radio waves) of that frequency (about 22 metres), the interaction is . See more
how to implement smart card authentication|smart card authentication step by