which statement is true regarding smart cards When users log in to the network remotely, they must provide their username, password, and smart card. Which two statements are true regarding your organization's security? (Choose two.) Feb 20, 2023 12:40 AM in response to samarat00. NFC, Near-field communication - Apple Developer. Near-field communication (NFC) enables devices within a few centimeters of each other to exchange information .
0 · what is smart card authentication
1 · va privacy and information security awareness rules of behavior
2 · mfa something you have know
3 · flashcard security practice test
The NFC Reader communicates with the 3DS via infrared. Smartphones that have IR blasters are pretty rare so even if you did emulate it with an NFC-enabled phone somehow you'd still need .
When users log in to the network remotely, they must provide their username, password, and smart card. Which two statements are true regarding your organization's security? (Choose two.)
Smart cards are typically used to provide secure, multi-factor authentication. Only users wit.
Smart cards are typically used to provide secure, multi-factor authentication. Only users with the smart card and who know the associated PIN number are allowed to authenticate. Computers .When users log in to the network remotely, they must provide their username, password, and smart card. Which two statements are true regarding your organization's security? (Choose two.)A smart card is a physical card that has an embedded integrated chip that acts as a security token. Smart cards are typically the same size as a driver's license or credit card and can be . Actual exam question from CompTIA's SY0-601. Question #: 623. Topic #: 1. [All SY0-601 Questions] Users have been issued smart cards that provide physical access to a .
what is smart card authentication
Which statement regarding smart cards is true? Multiple choice question. They are illegal in the United States. They operate through the use of a magnetic strip. They are not able to be used .
Successful attacks against smart cards have included power glitching; differential power analysis; and capping them then using an ion-beam microscope to read out the key bits . The false statement about Smart Cards from the options provided is C. 'The smart cards have magnetic strips that enable more security.' In actuality, smart cards use an .
Study with Quizlet and memorize flashcards containing terms like Which of the following does Windows use to manage and enforce what a user is authorized to access?, Which of the .Which of the following statements is true? a. Smart cards do not require an operating system. b. Smart cards and PCs use some operating system. c. COS is smart card operating system. d. .
va privacy and information security awareness rules of behavior
When users log in to the network remotely, they must provide their username, password, and smart card. Which two statements are true regarding your organization's security? (Choose two.)
Smart cards are typically used to provide secure, multi-factor authentication. Only users with the smart card and who know the associated PIN number are allowed to authenticate. Computers that require a smart card must have a smart card reader attached.When users log in to the network remotely, they must provide their username, password, and smart card. Which two statements are true regarding your organization's security? (Choose two.)A smart card is a physical card that has an embedded integrated chip that acts as a security token. Smart cards are typically the same size as a driver's license or credit card and can be made out of metal or plastic. Actual exam question from CompTIA's SY0-601. Question #: 623. Topic #: 1. [All SY0-601 Questions] Users have been issued smart cards that provide physical access to a building. The cards also contain tokens that can be used to access information systems.
mfa something you have know
Which statement regarding smart cards is true? Multiple choice question. They are illegal in the United States. They operate through the use of a magnetic strip. They are not able to be used as an ATM card. They store information that is useful to merchants. Here’s the best way to solve it. Solution. Let's evaluate each option: 1. Successful attacks against smart cards have included power glitching; differential power analysis; and capping them then using an ion-beam microscope to read out the key bits from the flash memory. Because the cards are always at risk of being stolen by an advanced attacker, each card is usually issued a unique key.
The false statement about Smart Cards from the options provided is C. 'The smart cards have magnetic strips that enable more security.' In actuality, smart cards use an embedded microchip for data storage and security functions, rather than a magnetic strip.Study with Quizlet and memorize flashcards containing terms like Which of the following does Windows use to manage and enforce what a user is authorized to access?, Which of the following BEST describes authorization?, Which of the following processes is used to prove a user's identity? and more.
Which of the following statements is true? a. Smart cards do not require an operating system. b. Smart cards and PCs use some operating system. c. COS is smart card operating system. d. The communication between reader and card is in full duplex mode. Posted under IT Fundamentals. Answer: (c).COS is smart card operating system.
When users log in to the network remotely, they must provide their username, password, and smart card. Which two statements are true regarding your organization's security? (Choose two.)Smart cards are typically used to provide secure, multi-factor authentication. Only users with the smart card and who know the associated PIN number are allowed to authenticate. Computers that require a smart card must have a smart card reader attached.When users log in to the network remotely, they must provide their username, password, and smart card. Which two statements are true regarding your organization's security? (Choose two.)A smart card is a physical card that has an embedded integrated chip that acts as a security token. Smart cards are typically the same size as a driver's license or credit card and can be made out of metal or plastic.
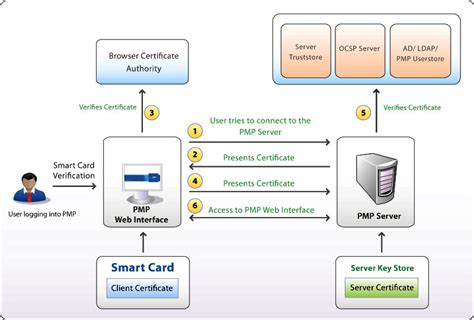
Actual exam question from CompTIA's SY0-601. Question #: 623. Topic #: 1. [All SY0-601 Questions] Users have been issued smart cards that provide physical access to a building. The cards also contain tokens that can be used to access information systems.Which statement regarding smart cards is true? Multiple choice question. They are illegal in the United States. They operate through the use of a magnetic strip. They are not able to be used as an ATM card. They store information that is useful to merchants. Here’s the best way to solve it. Solution. Let's evaluate each option: 1. Successful attacks against smart cards have included power glitching; differential power analysis; and capping them then using an ion-beam microscope to read out the key bits from the flash memory. Because the cards are always at risk of being stolen by an advanced attacker, each card is usually issued a unique key. The false statement about Smart Cards from the options provided is C. 'The smart cards have magnetic strips that enable more security.' In actuality, smart cards use an embedded microchip for data storage and security functions, rather than a magnetic strip.
flashcard security practice test

Study with Quizlet and memorize flashcards containing terms like Which of the following does Windows use to manage and enforce what a user is authorized to access?, Which of the following BEST describes authorization?, Which of the following processes is used to prove a user's identity? and more.
Because this tiny round device was found hidden inside of an NFC card reader .Download the Apps and you are good to go. If you don't have the XS, XS Max or XR, then to read NFC tags, you need to have installed iOS 11 or later and will need an App. NFC tag scanning with an App is only available on the iPhone 7, iPhone 7 Plus, iPhone 8, iPhone 8 .
which statement is true regarding smart cards|what is smart card authentication