rfid tags for access control RFID access control uses a system of tags, readers, and computer servers to allow access to verified users. The pros of RFID entry systems are ease of use, easy replacement, and practicality for doors, gates, vehicles, and elevators. Step 6: Tap on Payment default. Step 7: Select the app you use most often and want to pay with every time you tap your phone at a terminal. Step 8: Now, tap on Use default. Step 9: Choose .
0 · rfid gate access control systems
1 · rfid based door access control
2 · rfid access control wiring diagram
3 · rfid access control system price
4 · rfid access control system pdf
5 · rfid access control manual pdf
6 · rfid access control manual
7 · rfid access control instructions
Fongwah is a leading high technology manufacturer for developing&manufacturing RFID .
A complete RFID access control system typically consists of three main components: RFID tags, readers and writers, and management software. Users attach RFID tags as identification devices, while readers and writers send and receive signals to read tag information.
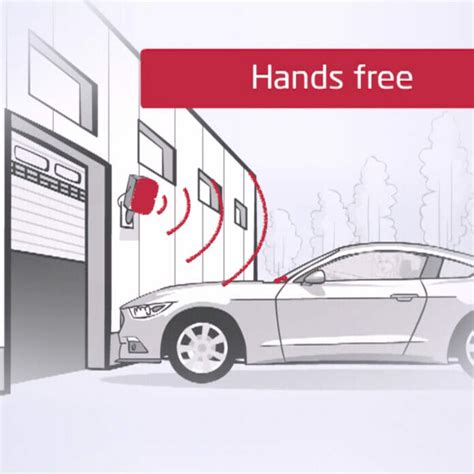
A complete RFID access control system typically consists of three main components: RFID tags, readers and writers, and management software. Users attach RFID tags as identification devices, while readers and writers send and receive signals to read tag information.
RFID access control uses a system of tags, readers, and computer servers to allow access to verified users. The pros of RFID entry systems are ease of use, easy replacement, and practicality for doors, gates, vehicles, and elevators.
RFID access control refers to systems that use RFID technology to allow or deny access to a particular area or facility. The system uses RFID key cards or tags, which carry embedded microchips that communicate wirelessly with RFID readers installed at multiple access points, such as doors or gates, to manage access.
Explore how car RFID tags are transforming vehicle access control! Delve into active & passive RFID, their pros & cons, and how video intercom systems enhance safety.
Access can be precisely managed and monitored by equipping doors and entry points with RFID readers and issuing RFID tags, key cards, or mobile devices with embedded RFID chips to authorized individuals.RFID access control systems work by utilizing a series of tags, readers and computer servers to grant door access to any authorized individuals in possession of valid credentials. RFID systems use passive tags or cards to grant access to authorized personnel, streamlining entry points and improving security. This technology is prevalent in various industries and applications, providing an effective and low-cost security solution. As already mentioned earlier, the RFID access control system consists of the following components: RFID tags, antennas, an RFID reader, and a transceiver. The RFID tags are attached to key cards or key fobs and hold unique identification data.
RFID tags consist of three key elements: a microchip, antenna and a substrate. The microchip within the tag is what stores and processes information, modulates and demodulates radio-frequency signals. And antenna enables the tag to receive and transmit the signal. RFID tags can be differentiated by their power supply. RFID access control uses a system of tags, readers, and computer servers to allow access to verified users. The pros of RFID entry systems are ease of use, easy replacement, and practicality for doors, gates, vehicles, and elevators.A complete RFID access control system typically consists of three main components: RFID tags, readers and writers, and management software. Users attach RFID tags as identification devices, while readers and writers send and receive signals to read tag information.
RFID access control uses a system of tags, readers, and computer servers to allow access to verified users. The pros of RFID entry systems are ease of use, easy replacement, and practicality for doors, gates, vehicles, and elevators. RFID access control refers to systems that use RFID technology to allow or deny access to a particular area or facility. The system uses RFID key cards or tags, which carry embedded microchips that communicate wirelessly with RFID readers installed at multiple access points, such as doors or gates, to manage access. Explore how car RFID tags are transforming vehicle access control! Delve into active & passive RFID, their pros & cons, and how video intercom systems enhance safety. Access can be precisely managed and monitored by equipping doors and entry points with RFID readers and issuing RFID tags, key cards, or mobile devices with embedded RFID chips to authorized individuals.
RFID access control systems work by utilizing a series of tags, readers and computer servers to grant door access to any authorized individuals in possession of valid credentials.
btc visa contactless card united kingdom
RFID systems use passive tags or cards to grant access to authorized personnel, streamlining entry points and improving security. This technology is prevalent in various industries and applications, providing an effective and low-cost security solution.
As already mentioned earlier, the RFID access control system consists of the following components: RFID tags, antennas, an RFID reader, and a transceiver. The RFID tags are attached to key cards or key fobs and hold unique identification data. RFID tags consist of three key elements: a microchip, antenna and a substrate. The microchip within the tag is what stores and processes information, modulates and demodulates radio-frequency signals. And antenna enables the tag to receive and transmit the signal. RFID tags can be differentiated by their power supply.
rfid gate access control systems
rfid based door access control
rfid access control wiring diagram
There are two popular RFID/NFC readers: RC522 and PN532 RFID/NFC reader. This tutorial focuses on RC522 RFID/NFC reader. PN532 RFID/NFC reader will be presented in an upcoming tutorial. RC522 RFID/NFC reader (also called .In order to read NFC tags, you need to create an instance of the NFC adapter class. This can be done using the getSystemService() method. Add the following code to your Activity’s onCreate() method.
rfid tags for access control|rfid access control system pdf