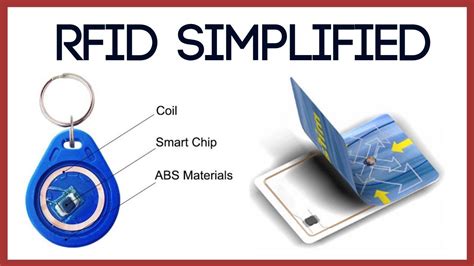
can an rfid chip A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a . $29.94
0 · where are rfid chips used
1 · types of rfid chips
2 · rfid chips in humans
3 · rfid chips for sale
4 · rfid chip pros and cons
5 · rfid chip meaning
6 · rfid chip manufacturing
7 · pros and cons of rfid
Payments: Accepts chip, swipe, and contactless payments including Apple Pay®, Google Pay® and Samsung Pay® Digital Receipts: Stores digital receipts and can email or text to customer-provided contact information Security: Clover Security Plus Connectivity: Micro USB for charging, Bluetooth® to mobile device for payments Battery life: Estimated 160 dip, 160 swipe, or 130 .
RFID stands for radio-frequency identification. A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID . See moreSome people are concerned that attackers could use a handheld device in a crowd to read RFID information from nearby credit cards with contactless payment information embedded in them. Identity thieves could read the same information from an RFID . See moreRFID tags can replace bar codes and QR codes. A bar code can only be read if the reader can visually see the bar code. RFID tags can be read if the reader is nearby, even if a bar code . See more Unlike barcodes that require line-of-sight scanning, RFID chips can be read from .
A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a . Unlike barcodes that require line-of-sight scanning, RFID chips can be read from a distance, without the need for direct visibility. This feature enables fast and efficient data capture, improving inventory management, asset tracking, and access control systems.
Security Risks. RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain access to a system or data.Rather than waiting to pay a toll at a tollbooth or shelling out coins at a token counter, passengers use RFID chip-embedded passes like debit cards. But would you entrust your medical history to an RFID tag?In October 2004, the FDA approved the USA's first RFID chips that can be implanted in humans. The 134 kHz RFID chips, from VeriChip Corp. can incorporate personal medical information and could save lives and limit injuries from errors in medical treatments, according to the company.
RFID (radio frequency identification) is a form of wireless communication that incorporates the use of electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum to uniquely identify an object, animal or person. Features. Like other types of radio frequency identification (RFID) products, some chips can operate without physical contact between the tag and the reader.
123. Everywhere a question like this is asked, I see people responding that (in a scenario where a card is used) the card does some processing with the data it receives/generates some data when it receives a signal. How is this possible without power? Radio frequency identification (RFID) is defined as a cutting-edge technology that harnesses radio waves to identify and monitor objects or people effortlessly without physical contact. RFID credit cards are considered to be as safe as EMV chip cards, and data theft concerning RFID cards is uncommon. This is because of how these cards transmit information and what.
A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a . Unlike barcodes that require line-of-sight scanning, RFID chips can be read from a distance, without the need for direct visibility. This feature enables fast and efficient data capture, improving inventory management, asset tracking, and access control systems. Security Risks. RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain access to a system or data.
Rather than waiting to pay a toll at a tollbooth or shelling out coins at a token counter, passengers use RFID chip-embedded passes like debit cards. But would you entrust your medical history to an RFID tag?In October 2004, the FDA approved the USA's first RFID chips that can be implanted in humans. The 134 kHz RFID chips, from VeriChip Corp. can incorporate personal medical information and could save lives and limit injuries from errors in medical treatments, according to the company.RFID (radio frequency identification) is a form of wireless communication that incorporates the use of electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum to uniquely identify an object, animal or person. Features. Like other types of radio frequency identification (RFID) products, some chips can operate without physical contact between the tag and the reader.
123. Everywhere a question like this is asked, I see people responding that (in a scenario where a card is used) the card does some processing with the data it receives/generates some data when it receives a signal. How is this possible without power?
Radio frequency identification (RFID) is defined as a cutting-edge technology that harnesses radio waves to identify and monitor objects or people effortlessly without physical contact.
where are rfid chips used
clone credit card rfid
cisco prime rfid tags
NFC XL Reader - Long range HF Reader/Writer. €98.00. Reference . LS-UFRXL-LIB. The NFC .What do you want to lock? You can have more than 100 ideas. Install the NFC Code Touch and the free Loxone software turns it into a complete access control system with many options: See more
can an rfid chip|where are rfid chips used