diagram of finger print smart card protocol This paper describes two types of smart card that use standard interfaces supported by most handheld devices, in lieu of those interfaces favored by most smart card readers. The paper . The NFL playoffs are here and Wild Card Weekend is well underway, with four of six games wrapped up over the weekend. On Saturday, action kicked off with C.J. Stroud and .
0 · Smart Card Technology and the FIDO Protocols
1 · Smart Card Handbook
2 · Smart Card Authentication for Mobile Devices
3 · Smart Card Architecture
For restaurants, scanning the NFC tag will open up their full menu. Moreover, some individuals use NFC tags as their virtual business cards. So just look for NFC tags. Then try to scan them. It’s a fast and easy way to test if .About NFC Tag Cloner. Clone NFC tags to another tag or to your phone. Clone NFC tags! And do it in an effective way which lightens up your day! Supported clone modes: - .
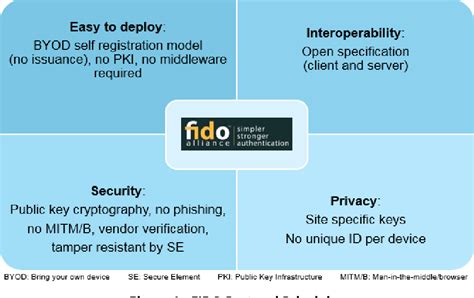
This paper describes two types of smart card that use standard interfaces supported by most handheld devices, in lieu of those interfaces favored by most smart card readers. The paper .Implementing the FIDO protocols with smart card technology can strengthen the security of the identity authentication process and bring the benefits of smart card technology to a wider audience.
The following sections in this article describe how Windows uses the smart card architecture to select the correct smart card reader software, provider, and credentials for a successful smart card sign-in:
This paper describes two types of smart card that use standard interfaces supported by most handheld devices, in lieu of those interfaces favored by most smart card readers. The paper explains how these forms of smart card can be applied to authenticate users on handheld devices and provides details of the solutions’ design and implementation.Different manufactures may adopt different card operating systems. This application note is based on a widely used CPU card made by Watchdata. It is a contact type card running TimeCOS. The ISO 7816 standard defines the necessary protocols to communicate with a smart card. The DS8007 is a multiprotocol, low-cost, dual, smart card interface that supports all ISO 7816, EMV™, and GSM11-11 requirements. This one mixed-signal peripheral manages all the details of the interface between a microcontroller and two, independent smart cards.
Smart Card (PIV Compatible) For an overview of the PIV features that became available with the 5.7.x firmware, see PIV Enhancements. The YubiKey 5 Series provides a PIV-compatible smart card application. PIV, or FIPS 201, is a US government standard.
The card reader talks to the smart card, asking the user to enter a code number or fingerprint or other body details to check who they are. The smart card checks the user’s details using secret codes and makes a digital signature or token to show who they are.
There are three sub types: Card Type A: operating voltage Vcc = 5.0V. Card Type B: operating voltage Vcc = 3.0V. Card Type C: operating voltage Vcc = 1.8V (new cards ) Since there is no external and visible way to identify the card a.Smart Card Technology Capabilities 4 Definition • What is a smart card? – A plastic card with an embedded microprocessor chip. • What is the essence of a smart card? – Authentication – Data storage – Validation – Self-lock mechanism
When logical channels are used, upto 19 applications in a single card can exchange data directly with the terminal. The chapter describes main features some protocols that includes TCP/IP protocol, HTTP protocol and Bearer Independent Protocol (BIP) and connecting terminals to higher-level systems.Implementing the FIDO protocols with smart card technology can strengthen the security of the identity authentication process and bring the benefits of smart card technology to a wider audience.The following sections in this article describe how Windows uses the smart card architecture to select the correct smart card reader software, provider, and credentials for a successful smart card sign-in:This paper describes two types of smart card that use standard interfaces supported by most handheld devices, in lieu of those interfaces favored by most smart card readers. The paper explains how these forms of smart card can be applied to authenticate users on handheld devices and provides details of the solutions’ design and implementation.
Smart Card Technology and the FIDO Protocols
Different manufactures may adopt different card operating systems. This application note is based on a widely used CPU card made by Watchdata. It is a contact type card running TimeCOS. The ISO 7816 standard defines the necessary protocols to communicate with a smart card.
Smart Card Handbook
The DS8007 is a multiprotocol, low-cost, dual, smart card interface that supports all ISO 7816, EMV™, and GSM11-11 requirements. This one mixed-signal peripheral manages all the details of the interface between a microcontroller and two, independent smart cards.Smart Card (PIV Compatible) For an overview of the PIV features that became available with the 5.7.x firmware, see PIV Enhancements. The YubiKey 5 Series provides a PIV-compatible smart card application. PIV, or FIPS 201, is a US government standard. The card reader talks to the smart card, asking the user to enter a code number or fingerprint or other body details to check who they are. The smart card checks the user’s details using secret codes and makes a digital signature or token to show who they are. There are three sub types: Card Type A: operating voltage Vcc = 5.0V. Card Type B: operating voltage Vcc = 3.0V. Card Type C: operating voltage Vcc = 1.8V (new cards ) Since there is no external and visible way to identify the card a.
Smart Card Technology Capabilities 4 Definition • What is a smart card? – A plastic card with an embedded microprocessor chip. • What is the essence of a smart card? – Authentication – Data storage – Validation – Self-lock mechanism
how to read nfc uid
google pixel 4 nfc read error
Smart Card Authentication for Mobile Devices
Amiibo data are stored on the physical Amiibo as a .bin file..Bin file - raw data from physical Amiibo.NFC file - the file needed to write to an NFC tag/card or send via nfc to your switch, this emulates a physical Amiibo.. Note: You won't .
diagram of finger print smart card protocol|Smart Card Technology and the FIDO Protocols