understand smart card authentication Discover the benefits, challenges, and best practices for implementation. Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and . You need the make a BAC (Basic Access Control) against your epassport to be able to read the basic informations printed on the passport (Country, Name, Surname, Nationality, Date of birth, Sex.) and the MRZ .
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
When an NFC tag is detected, the Android system will send an NFC intent to your app. You need to override the onNewIntent() method of your Activity to handle the NFC intent. Here is an example .
This section describes what a smart card is and how smart card authentication works. It .How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.This section describes what a smart card is and how smart card authentication works. It describes the tools that you can use to read and manipulate smart card content. It also provides sample use cases and describes the setup of both the IdM server and IdM client for smart card authentication. In its most simple form, public key authentication as follows: The server sends Alice a random string (nonce). Alice encrypts the nonce with her private key and sends it to the server along with her certificate.
Discover the benefits, challenges, and best practices for implementation. Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and .
Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers. Understanding Smart Card Authentication: Smart Card Authentication is how identity is checked using a smart card. The smart card has a microchip that can securely store and work with information. Comparing virtual smart cards with physical smart cards: compares properties, functional aspects, security, and cost. Authentication design options: describes how passwords, smart cards, and virtual smart cards can be used to reach authentication goals in .
Smart Card Authentication is a means of verifying users into enterprise resources using a physical card in tandem with a smart card reader and software.
A smart card is a secure microcontroller that is typically used for generating, storing and operating on cryptographic keys. Smart card authentication provides users with smart card devices for the purpose of authentication. Users connect their smart card to a host computer.The owner must physically have the smart card, and they must know the PIN to unlock it. This provides a higher degree of security than single-factor authentication (such as just using a password). In this page, we describe how to enable smart card authentication on Ubuntu. Note:How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.This section describes what a smart card is and how smart card authentication works. It describes the tools that you can use to read and manipulate smart card content. It also provides sample use cases and describes the setup of both the IdM server and IdM client for smart card authentication.
In its most simple form, public key authentication as follows: The server sends Alice a random string (nonce). Alice encrypts the nonce with her private key and sends it to the server along with her certificate. Discover the benefits, challenges, and best practices for implementation. Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and . Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers. Understanding Smart Card Authentication: Smart Card Authentication is how identity is checked using a smart card. The smart card has a microchip that can securely store and work with information.
Comparing virtual smart cards with physical smart cards: compares properties, functional aspects, security, and cost. Authentication design options: describes how passwords, smart cards, and virtual smart cards can be used to reach authentication goals in .
smart card multi factor authentication
smart card identity
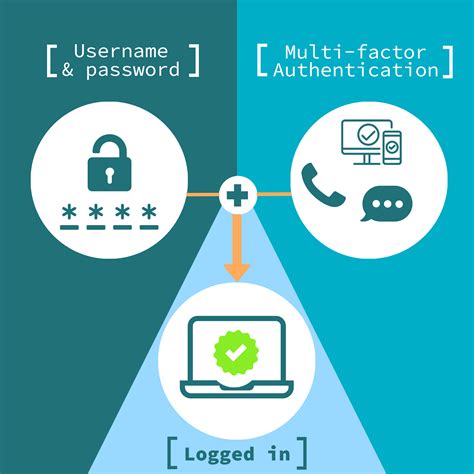

Smart Card Authentication is a means of verifying users into enterprise resources using a physical card in tandem with a smart card reader and software.
A smart card is a secure microcontroller that is typically used for generating, storing and operating on cryptographic keys. Smart card authentication provides users with smart card devices for the purpose of authentication. Users connect their smart card to a host computer.

smart card based identification system
smart card authentication step by
You can listen to live Auburn Tigers games online or on the radio dial. With 54 stations in the network, the Auburn Sports Network represents one of the biggest and most-listened to college sports network in the South. All home and away .
understand smart card authentication|enable smart card log on