simple lightweight rfid reader protocol In brief, the BOF is to explore whether a reader control protocol should be developed for RFID readers. Issues relating to tag/reader RF and high-level APIs are out of scope. Barvick presented the agenda: a status update, several presentations, followed by an hour of discussion. This app was designed to allow users to read the public data stored on their NFC-compliant EMV banking cards, such as credit cards. EMV (Europay, Mastercard, and Visa) is a global standard for interbank transactions that .Learn how to turn your smartphone into an NFC card; easily make payments, access buildings, and more with this step-by-step guide. See more
0 · rfid encryption protocol
1 · lightweight rfid authentication
What is an NFC SE SIM card? An NFC SE (Near Field Communication Secure .I have uploaded every Amiibo .Bin and .NFC file I could get my hands on. I have NOT tested all of these but I have tested most, so please let . See more
This draft specifies a controller-to-reader protocol (the Simple Lightweight RFID Reader Protocol, or SLRRP (pronounced 'slurp') for use in an IP-based network to convey configuration, control, status, and tag information to and from readers.In brief, the BOF is to explore whether a reader control protocol should be developed for RFID readers. Issues relating to tag/reader RF and high-level APIs are out of scope. Barvick .This draft specifies a controller-to-reader protocol (the Simple Lightweight RFID Reader Protocol, or SLRRP (pronounced 'slurp') for use in an IP-based network to convey configuration, control, status, and tag information to and from readers.In brief, the BOF is to explore whether a reader control protocol should be developed for RFID readers. Issues relating to tag/reader RF and high-level APIs are out of scope. Barvick presented the agenda: a status update, several presentations, followed by an hour of discussion.
This paper studies the problem of anonymous authentication. Since low-cost tags have extremely limited hardware resource, we propose an asymmetric design principle that pushes most complexity to more powerful RFID readers. With this principle, we develop a lightweight technique that generates dynamic tokens for anonymous authentication. To maintain security in RFID systems, there is a need to use some lightweight authentication protocols, as RFID tags have limited memory and less computation capabilities. This paper reviewed the three RFID-based lightweight authentication protocols, i.e. LRSAS + , LRARP, and LRARP + .This draft specifies the Simple Lightweight RFID Reader Protocol, or SLRRP (pronounced 'slurp'), to be used to convey configuration, control, status, and tag information between controllers and readers in an IP-based network. Table of Contents 1. Introduction . . Based on the algorithm, this paper first designed a lightweight RFID security authentication protocol LRSAS, and then verified its security from seven security requirements, including data confidentiality and integrity, replay attack, impersonation attack, tracking attack, desynchronization attack, denial of service attack, and forward security .
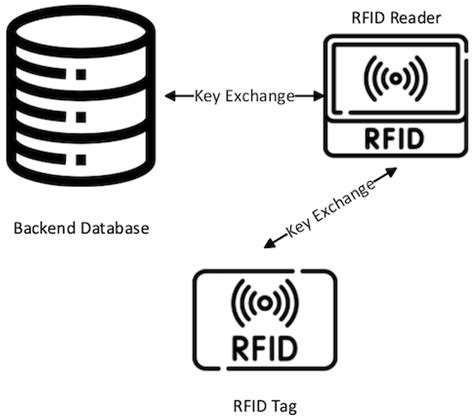
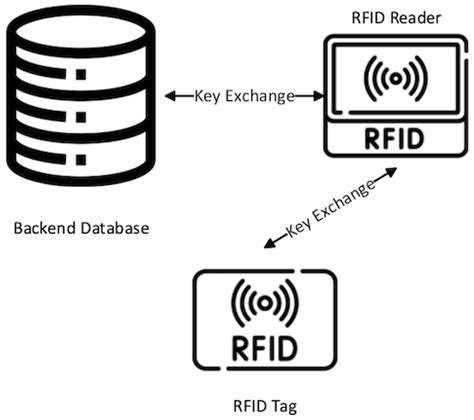
some simple and efficient hash-based lightweight RFID authentication protocols, like a lightweight RFID mutual authentication protocol with cache in the reader In order to address the security issues in low‐cost RFID, some simple and efficient hash‐based lightweight RFID authentication protocols, like a lightweight RFID mutual authentication protocol with cache in the reader (LRMAPC), are presented.This protocol exploits an on-chip CRC function and a pseudorandom number generator to ensure the anonymity and freshness of communications between reader and tag. It provides forward security and confidential communication.Thus, this research analyzes the existing methods for controlling RFID tag memory access, and then proposes a light-weight RFID device interface, called SRP (Simple Reader Protocol). SRP specifies the message formats, supports access operations, and enables the RFID reader configuration about RFID tag memory access.
This draft specifies a controller-to-reader protocol (the Simple Lightweight RFID Reader Protocol, or SLRRP (pronounced 'slurp') for use in an IP-based network to convey configuration, control, status, and tag information to and from readers.In brief, the BOF is to explore whether a reader control protocol should be developed for RFID readers. Issues relating to tag/reader RF and high-level APIs are out of scope. Barvick presented the agenda: a status update, several presentations, followed by an hour of discussion.
This paper studies the problem of anonymous authentication. Since low-cost tags have extremely limited hardware resource, we propose an asymmetric design principle that pushes most complexity to more powerful RFID readers. With this principle, we develop a lightweight technique that generates dynamic tokens for anonymous authentication. To maintain security in RFID systems, there is a need to use some lightweight authentication protocols, as RFID tags have limited memory and less computation capabilities. This paper reviewed the three RFID-based lightweight authentication protocols, i.e. LRSAS + , LRARP, and LRARP + .This draft specifies the Simple Lightweight RFID Reader Protocol, or SLRRP (pronounced 'slurp'), to be used to convey configuration, control, status, and tag information between controllers and readers in an IP-based network. Table of Contents 1. Introduction . . Based on the algorithm, this paper first designed a lightweight RFID security authentication protocol LRSAS, and then verified its security from seven security requirements, including data confidentiality and integrity, replay attack, impersonation attack, tracking attack, desynchronization attack, denial of service attack, and forward security .
some simple and efficient hash-based lightweight RFID authentication protocols, like a lightweight RFID mutual authentication protocol with cache in the reader In order to address the security issues in low‐cost RFID, some simple and efficient hash‐based lightweight RFID authentication protocols, like a lightweight RFID mutual authentication protocol with cache in the reader (LRMAPC), are presented.This protocol exploits an on-chip CRC function and a pseudorandom number generator to ensure the anonymity and freshness of communications between reader and tag. It provides forward security and confidential communication.
honda rfid chip
rfid encryption protocol
lightweight rfid authentication
TL;DR: Phone can emulate UID, but not nfc chip type. Will access systems still accept it? I recently got some of my old phones rooted, and got the Card Emulator Pro app installed. .
simple lightweight rfid reader protocol|lightweight rfid authentication