internal authentication smart card Smart cards are tamper-resistant portable storage devices that can enhance the security of tasks such as authenticating clients, signing code, securing e-mail, and signing in with a Windows domain account. 512 GB. 4800 mAh. Check price. List of best smartphones with NFC. Latest cell phones with NFC. Find out which mobile phone has NFC feature. Phones from all brands: Samsung, apple, xiaomi, huawei and more. Which android or iphone .These selections of affordable Samsung NFC phones come with useful features and decent specs, from large battery capacity to massive phone RAM size for multitasking. Galaxy A73 5G. Galaxy A53 5G. Galaxy A23 5G. Galaxy A33 5G.NFC Tools is a simple app that lets you read, write, or erase NFC tags. Once you open the app, you see 4 tabs on the top – Read, Write, Others, Tasks. The Read option lets you scan and read the details of the tag such as the serial number and type of the tag. With the Write option, you can write information . See more
0 · Understanding Smart Card Authenticatio
1 · Smart Card Technical Reference
2 · Smart Card Architecture
3 · How does Smart Card Authentication w
4 · How Smart Card Sign
5 · Chapter 1. Understanding smart card au
Step 1: Materials List. Everything you need for this project can be bought on E-Bay or in many Chinese e-shops like dealextreme etc. For this project you'll .
Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that .
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers.
Smart cards provide an easy and movable way to prove who you are, without needing to remember hard passwords. Smart card security can be combined with other authentication methods like personal identification numbers or biometrics for stronger protection. Implementing Smart Card Authentication: Smart cards are tamper-resistant portable storage devices that can enhance the security of tasks such as authenticating clients, signing code, securing e-mail, and signing in with a Windows domain account.
Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation. Smart cards come in two primary flavors: Memory cards & Microprocessor cards (pg. 18). The very first smart cards were memory cards with re-write protected cells that could only be written to once (pg. 6). Authentication refers to the process that verifies the identity of a user, system, or device before granting access to data or resources. It's an essential layer of protection in any network monitoring program. So, what type of device is used for user authentication? It depends on the authentication processes in place.
Understanding smart card authentication. PDF. Authentication based on smart cards is an alternative to passwords. You can store user credentials on a smart card in the form of a private key and a certificate, and special software and hardware is used to access them.
To enable smart card authentication we should rely on a module that allows PAM supported systems to use X.509 certificates to authenticate logins. The module relies on a PKCS#11 library, such as opensc-pkcs11 to access the smart card for the credentials it will need.How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers.
Smart cards provide an easy and movable way to prove who you are, without needing to remember hard passwords. Smart card security can be combined with other authentication methods like personal identification numbers or biometrics for stronger protection. Implementing Smart Card Authentication:
Smart cards are tamper-resistant portable storage devices that can enhance the security of tasks such as authenticating clients, signing code, securing e-mail, and signing in with a Windows domain account. Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation. Smart cards come in two primary flavors: Memory cards & Microprocessor cards (pg. 18). The very first smart cards were memory cards with re-write protected cells that could only be written to once (pg. 6).
Authentication refers to the process that verifies the identity of a user, system, or device before granting access to data or resources. It's an essential layer of protection in any network monitoring program. So, what type of device is used for user authentication? It depends on the authentication processes in place.Understanding smart card authentication. PDF. Authentication based on smart cards is an alternative to passwords. You can store user credentials on a smart card in the form of a private key and a certificate, and special software and hardware is used to access them.
lecteur badge nfc

Understanding Smart Card Authenticatio
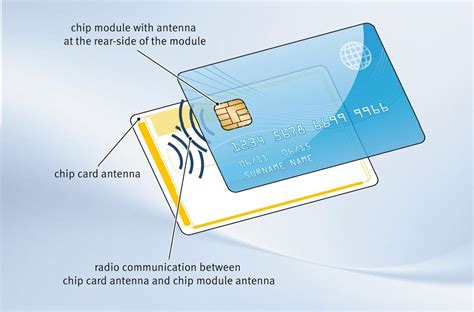
Here are some common reasons why you might not be able to read NFC tags: Incompatibility with Device: Not all devices are NFC-enabled or support all types of NFC tags. .Fitbit Versa 4: Best Budget Smartwatch With NFC. Fossil Gen 6 Smartwatch: Best Stylish Smartwatch. Samsung Galaxy Watch 5: Best Overall. Ticwatch .
internal authentication smart card|Understanding Smart Card Authenticatio