cac/piv smart cards Agency security is enhanced when PIV credentials are used for authentication to agency systems and facilities. PIV credentials allow for . See more To use NFC Tag Reader in iOS 17 on your iPhone, follow the steps given below-. Open the Settings app on your iPhone. In the Settings, scroll down to find Control Center. Open the Control Center by tapping on it. Now, .
0 · yubikey smart card deployment guide
1 · what is smart card authentication
2 · what is piv cac card
3 · what is a piv badge
4 · what are piv compliant credentials
5 · smart card piv compatible
6 · smart card piv authentication
7 · smart card identification
And we’re proud to be the hometown station for Auburn sports: Auburn University football, basketball and baseball plus Auburn High football. War Eagle! Twitter: @wings943fm. Language: English. Contact: WGZZ-FM P.O. Box 950 Auburn, .
IDManagement.gov is a collaboration between the Federal CIO Council and GSA to develop and share leading practices in protecting federal IT systems. See moreThis Personal Identity Verification (PIV) 101 is intended to help you understand the purpose and uses of a PIV credential at your organization. . See more
A PIV credential is a U.S. federal government-wide credential used to access federally controlled facilities and information systems at the appropriate security level. PIV . See moreAgency security is enhanced when PIV credentials are used for authentication to agency systems and facilities. PIV credentials allow for . See more
This 101 covers PIV credential basics, including: 1. What PIV is, contains, and looks like. 2. The basics of getting started with PIV credentials. . See moreYour PIV/CAC credential contains an authentication certificate key pair (public and private) for smart card logon. Using a PIV/CAC key pair is very similar to using a self-signed key pair for SSH.Like the CAC, the PIV card is also a smartcard that contains a certificate and a private key to .Cardholder Unique Identifier (CHUID), which is a digitally signed Federal Agency Smart Card Number (FASC-N) plus other data that can be used. Card Authentication, which is a certificate and key pair that can be used to verify that the PIV credential was issued by an authorized entity, has not expired, and has not been revoked.
Your PIV/CAC credential contains an authentication certificate key pair (public and private) for smart card logon. Using a PIV/CAC key pair is very similar to using a self-signed key pair for SSH.
Like the CAC, the PIV card is also a smartcard that contains a certificate and a private key to be used to gain access to computers, networks, and online resources. PIV is the standard method for strong authentication within the US Federal government.
All Army personnel (previously only Dual Persona) users have to activate the PIV on their CACs (click these 64bit / 32bit links for specific instructions). Previously, only Dual Persona user needed to activate their PIV to be able to access their Enterprise Email account (s).Common Access Card (CAC) The CAC, a "smart" card about the size of a credit card, is the standard identification for active duty uniformed Service personnel, Selected Reserve, DoD civilian employees, and eligible contractor personnel.Common Access Card (CAC) Security. The CAC — which is roughly the size of a standard credit card — stores 144K of data storage and memory on a single integrated circuit chip (ICC). This CAC technology allows for rapid authentication and .These Windows Domain configuration guides will help you configure your Windows network domain for smart card logon using PIV credentials. There are many useful pages and technical articles available online that include details on configurations and using generic smart cards.
YubiKey 5 NFC, YubiKey 5 Nano, YubiKey 5C, and YubiKey 5C Nano provide Smart Card functionality based on the Personal Identity Verification (PIV) interface specified in NIST SP 800-73, “Cryptographic Algorithms and Key Sizes for PIV.”CAC and PIV cards are types of smart cards that contain embedded microchips, which store digital certificates and cryptographic keys used for authentication and encryption purposes.This Standard satisfies the control objectives, security requirements, and technical interoperability requirements of [HSPD-12]. The Standard specifies implementation of identity credentials on integrated circuit cards for use in a Federal personal identity verification system.Cardholder Unique Identifier (CHUID), which is a digitally signed Federal Agency Smart Card Number (FASC-N) plus other data that can be used. Card Authentication, which is a certificate and key pair that can be used to verify that the PIV credential was issued by an authorized entity, has not expired, and has not been revoked.
Your PIV/CAC credential contains an authentication certificate key pair (public and private) for smart card logon. Using a PIV/CAC key pair is very similar to using a self-signed key pair for SSH.Like the CAC, the PIV card is also a smartcard that contains a certificate and a private key to be used to gain access to computers, networks, and online resources. PIV is the standard method for strong authentication within the US Federal government. All Army personnel (previously only Dual Persona) users have to activate the PIV on their CACs (click these 64bit / 32bit links for specific instructions). Previously, only Dual Persona user needed to activate their PIV to be able to access their Enterprise Email account (s).

Common Access Card (CAC) The CAC, a "smart" card about the size of a credit card, is the standard identification for active duty uniformed Service personnel, Selected Reserve, DoD civilian employees, and eligible contractor personnel.Common Access Card (CAC) Security. The CAC — which is roughly the size of a standard credit card — stores 144K of data storage and memory on a single integrated circuit chip (ICC). This CAC technology allows for rapid authentication and .These Windows Domain configuration guides will help you configure your Windows network domain for smart card logon using PIV credentials. There are many useful pages and technical articles available online that include details on configurations and using generic smart cards.
YubiKey 5 NFC, YubiKey 5 Nano, YubiKey 5C, and YubiKey 5C Nano provide Smart Card functionality based on the Personal Identity Verification (PIV) interface specified in NIST SP 800-73, “Cryptographic Algorithms and Key Sizes for PIV.”CAC and PIV cards are types of smart cards that contain embedded microchips, which store digital certificates and cryptographic keys used for authentication and encryption purposes.
yubikey smart card deployment guide
what is smart card authentication
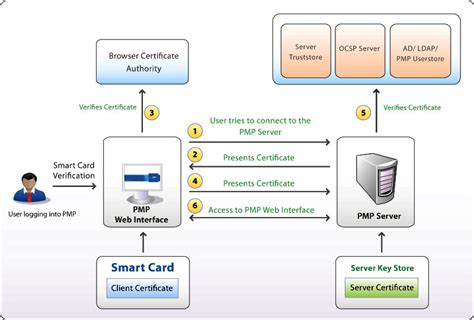
what is piv cac card
what is a piv badge
what are piv compliant credentials

Support both background and in-app tag reading. Your app must still provide an in-app way to scan tags, for people with devices that don’t support background tag reading. Platform considerations. No additional considerations for iOS or .
cac/piv smart cards|smart card identification