create access smart cards Virtual smart cards are functionally similar to physical smart cards, appearing in Windows as smart cards that are always-inserted. Virtual smart cards can be used for authentication to external resources, protection of data by . NFL Playoff Picture. Stay up to date with your favorite team to see if they have a chance to make the 2024 playoffs. Seven teams from each conference will make it to the postseason. Check out .
0 · Virtual Smart Card Overview
1 · Use Virtual Smart Cards
2 · Unveiling the Different Types of Smart C
3 · Understanding Smart Card Authentication
4 · Personal Identity Verification Card 101
5 · How Do I Read a Smart Card in Window
6 · Get Started with Virtual Smart Cards
How to use Quick Share: Find the file, photo, or content you want to share. Tap on the Share button. Select Quick Share. Your device will start .
Virtual smart cards are functionally similar to physical smart cards, appearing in . By utilizing Trusted Platform Module (TPM) devices that provide the same cryptographic capabilities as physical smart cards, virtual smart cards accomplish the three key properties that are desired by smart cards: nonexportability, isolated cryptography, and . Virtual smart cards are functionally similar to physical smart cards, appearing in Windows as smart cards that are always-inserted. Virtual smart cards can be used for authentication to external resources, protection of data by . This topic contains information about the following phases in a virtual smart card lifecycle: Create and personalize virtual smart cards; Provision virtual smart cards; Maintain virtual smart cards; Create and personalize virtual smart cards. A .
Smart cards can process data, carry out commands, and secure information thanks to recent advancements in circuit chip technology. In this comprehensive guide, we’ll dive into different types of smart cards for access control, their functionalities, and their uses in . The basic process of using virtual smart cards involves three steps: Create the certificate template needed for virtual smart card enrollment. Create the virtual smart card powered by the TPM. Enroll for the TPM virtual smart card certificate. To verify that you have a TPM installed, run tpm.msc. Note the following information:
To do this, follow these step-by-step instructions: 1. Open the Control Panel by clicking on the Start menu and selecting Control Panel. 2. In the Control Panel, navigate to the “Hardware and Sound” section and click on “Device Manager.” 3. In the Device Manager window, expand the “Smart card readers” category. 4. This is my first blog and today I’ll share with you how to configure a Hyper-V environment in order to enable virtual smart card logon to VM guests by leveraging a new Windows 10 feature: virtual Trusted Platform Module (TPM).
Virtual Smart Card Overview
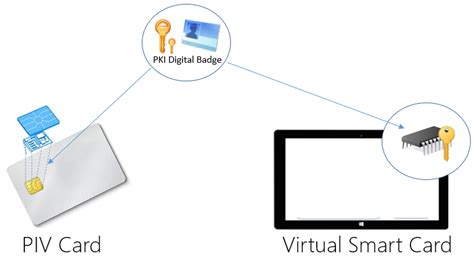
The process: The user puts the smart card into a card reader hooked up to the device or system they want to use. The card reader talks to the smart card, asking the user to enter a password or give fingerprints to prove who they are. In this post, we will walk through step-by-step how you can set up and configure new or existing Microsoft PKI to support PIV smart card authentication including setting up an OCSP responder, proper configuration of Active Directory, domain controllers, certificate templates, group policy, and WorkSpaces. Virtual smart cards that utilize a TPM provide the three main security principles of traditional smart cards: nonexportability, isolated cryptography, and anti-hammering. Virtual smart cards are less expensive to implement and more convenient for users.
By utilizing Trusted Platform Module (TPM) devices that provide the same cryptographic capabilities as physical smart cards, virtual smart cards accomplish the three key properties that are desired by smart cards: nonexportability, isolated cryptography, and .
Virtual smart cards are functionally similar to physical smart cards, appearing in Windows as smart cards that are always-inserted. Virtual smart cards can be used for authentication to external resources, protection of data by . This topic contains information about the following phases in a virtual smart card lifecycle: Create and personalize virtual smart cards; Provision virtual smart cards; Maintain virtual smart cards; Create and personalize virtual smart cards. A . Smart cards can process data, carry out commands, and secure information thanks to recent advancements in circuit chip technology. In this comprehensive guide, we’ll dive into different types of smart cards for access control, their functionalities, and their uses in . The basic process of using virtual smart cards involves three steps: Create the certificate template needed for virtual smart card enrollment. Create the virtual smart card powered by the TPM. Enroll for the TPM virtual smart card certificate. To verify that you have a TPM installed, run tpm.msc. Note the following information:
To do this, follow these step-by-step instructions: 1. Open the Control Panel by clicking on the Start menu and selecting Control Panel. 2. In the Control Panel, navigate to the “Hardware and Sound” section and click on “Device Manager.” 3. In the Device Manager window, expand the “Smart card readers” category. 4. This is my first blog and today I’ll share with you how to configure a Hyper-V environment in order to enable virtual smart card logon to VM guests by leveraging a new Windows 10 feature: virtual Trusted Platform Module (TPM). The process: The user puts the smart card into a card reader hooked up to the device or system they want to use. The card reader talks to the smart card, asking the user to enter a password or give fingerprints to prove who they are.
In this post, we will walk through step-by-step how you can set up and configure new or existing Microsoft PKI to support PIV smart card authentication including setting up an OCSP responder, proper configuration of Active Directory, domain controllers, certificate templates, group policy, and WorkSpaces.
Use Virtual Smart Cards

macrodroid nfc tag
Unveiling the Different Types of Smart C
Following are the features of NFC type-3 Tag: • Standard: ISO-18092, JIS-X-6319-4 • Memory Size: 1/4/9 KB • Speed: 212 or 424 kbps • Data Access: Read/Write or Read Only • Collision mechanism: Anti-collision support available • Compliant Products: Sony . See more
create access smart cards|Personal Identity Verification Card 101