rfid tags security A simple introduction to how RF and RFID tags are used in smart cards, toll collection, shop security, and other everyday applications.
Location Search. Auburn, Georgia Radio Stations. We found 76 FM radio stations and 59 AM radio stations in the Auburn, GA area.
0 · two types of rfid tags
1 · rfid tags and their uses
2 · rfid radio frequency identification tags
3 · rfid privacy and security issues
4 · retail anti theft security tags
5 · radio frequency identification tags are
6 · problems with rfid technology
7 · problems with rfid
August 31, 2023 4:00 pm CT. Nothing beats a Saturday listening to Auburn Sports Network’s all-day coverage of Auburn Tigers football in the fall. This season’s lineup within the Auburn Sports Network changes slightly, as Andy .

two types of rfid tags
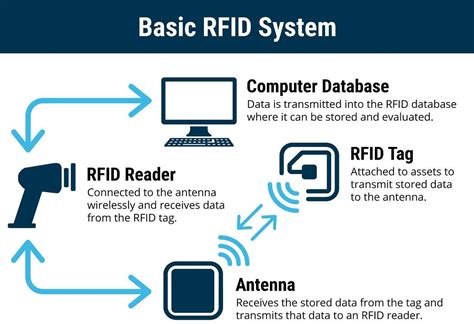
RFID stands for radio-frequency identification. A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID . See moreSome people are concerned that attackers could use a handheld device in a crowd to read RFID information from nearby credit cards with contactless payment information embedded in them. Identity thieves could read the same information from an RFID . See moreRFID tags can replace bar codes and QR codes. A bar code can only be read if the reader can visually see the bar code. RFID tags can be read if the reader is nearby, even if a bar code . See more A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a .
So, how can you protect your information from these threats? 1. Switches require that someone physically press a button, or a switch, in order to activate the tag. Meaning that the tag cannot be read until the person responsible for it has consented to it being read. A simple introduction to how RF and RFID tags are used in smart cards, toll collection, shop security, and other everyday applications. RFID tags have become essential in boosting security and creating smooth access systems in many areas. These small yet powerful tools are often used in systems that control access, letting only authorized people enter restricted zones.
This post aims to highlight several important RFID related security issues. RFID Counterfeiting: depending on the computing power, RFID can be classified into three categories: Basic tags; Tags that uses symmetric keys; Tags that uses public-key; Since basic tags do not use any encryption, they can be counterfeited easily.RFID attacks occur when an unauthorized individual intercepts or manipulates the signals transmitted between RFID tags and readers. There are several techniques commonly used by attackers to exploit RFID vulnerabilities. RFID tags are a type of tracking system that use radio frequency to search, identify, track, and communicate with items or individuals. Essentially, RFID tags, like barcodes, are smart labels that can store a range of information from serial numbers to a short description, and even pages of data. This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.
RFID tags are made up of an integrated circuit (IC), an antenna and a substrate. The part of an RFID tag that encodes identifying information is called the RFID inlay. There are two main types of RFID tags: Active RFID. An active RFID tag has its own power source, often a . An introduction to RFID security. 21 July 2023. This blog is intended for individuals with a technical background eager to explore Radio Frequency IDentification (RFID) technology and its implementation. Whether you are interested in the basics of RFID or looking to enhance the security of your current RFID system, this blog is your go-to resource. A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a .
So, how can you protect your information from these threats? 1. Switches require that someone physically press a button, or a switch, in order to activate the tag. Meaning that the tag cannot be read until the person responsible for it has consented to it being read. A simple introduction to how RF and RFID tags are used in smart cards, toll collection, shop security, and other everyday applications.
RFID tags have become essential in boosting security and creating smooth access systems in many areas. These small yet powerful tools are often used in systems that control access, letting only authorized people enter restricted zones.
This post aims to highlight several important RFID related security issues. RFID Counterfeiting: depending on the computing power, RFID can be classified into three categories: Basic tags; Tags that uses symmetric keys; Tags that uses public-key; Since basic tags do not use any encryption, they can be counterfeited easily.

RFID attacks occur when an unauthorized individual intercepts or manipulates the signals transmitted between RFID tags and readers. There are several techniques commonly used by attackers to exploit RFID vulnerabilities.
RFID tags are a type of tracking system that use radio frequency to search, identify, track, and communicate with items or individuals. Essentially, RFID tags, like barcodes, are smart labels that can store a range of information from serial numbers to a short description, and even pages of data. This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.RFID tags are made up of an integrated circuit (IC), an antenna and a substrate. The part of an RFID tag that encodes identifying information is called the RFID inlay. There are two main types of RFID tags: Active RFID. An active RFID tag has its own power source, often a .
rfid tags and their uses
rfid programming toyota key chip
Auburn Tigers. Get live coverage of SEC college football games with home and away feeds for every team on SiriusXM, including the Auburn Tigers. Hear exclusive interviews with Auburn players and coaches, plus expert analysis .Statewide coverage is the hallmark of the Auburn Sports Network's exclusive coverage of Auburn football. All home and away games are broadcast across the entire state .
rfid tags security|two types of rfid tags