smart cards for authentication Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers. $23.98
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
9. Trendhim RFID & NFC Blocking Card. Next up is Trendhim, another reliable .
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.
Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers.
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.
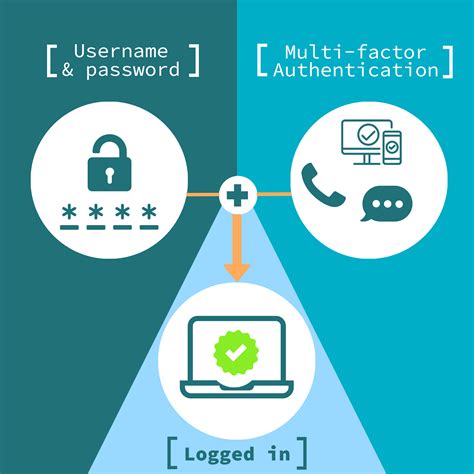
Virtual smart cards offer comparable security benefits to conventional smart cards by using two-factor authentication. The technology also offers more convenience for users and has a lower cost to deploy.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.Smart card authentication requires two things: the smart card itself and a pin entered by the user. With smart cards there are two different ways to authenticate yourself into a system, there is either contact or contactless smart card readers.Offering a range of certificate-based PKI smart cards with strong multi-factor authentication. Our Smart card authentication meets the highest security standards!
Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications. Smart cards let you use extra checks too, like a code or your body, to make authentication even safer. Smart cards use complex codes to keep data safe and stop unwanted users. Smart cards provide an easy and movable way to prove who you are, without needing to remember hard passwords.
Smart card authentication is a security technology that uses smart cards, which are small plastic cards with embedded microchips, to prove a user's identity. The microchip securely stores the user's authentication credentials, such as a personal identification number (PIN), digital certificates, and biometric data.Smart cards, such as debit cards, are often used with a personal identification number (PIN). Organizations also use them for security purposes, as MFA tokens and for authenticating single sign-on users and enabling passwordless authentication. Types of smart cardsStoring the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers.
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. Virtual smart cards offer comparable security benefits to conventional smart cards by using two-factor authentication. The technology also offers more convenience for users and has a lower cost to deploy.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.Smart card authentication requires two things: the smart card itself and a pin entered by the user. With smart cards there are two different ways to authenticate yourself into a system, there is either contact or contactless smart card readers.
rfid-chip zerstören magnet
Offering a range of certificate-based PKI smart cards with strong multi-factor authentication. Our Smart card authentication meets the highest security standards! Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.
Smart cards let you use extra checks too, like a code or your body, to make authentication even safer. Smart cards use complex codes to keep data safe and stop unwanted users. Smart cards provide an easy and movable way to prove who you are, without needing to remember hard passwords.
Smart card authentication is a security technology that uses smart cards, which are small plastic cards with embedded microchips, to prove a user's identity. The microchip securely stores the user's authentication credentials, such as a personal identification number (PIN), digital certificates, and biometric data.
switzerland rfid chip
smart card multi factor authentication
smart card identity
how to find rfid chips
The latest SDHC card by Toshiba offers a world’s first innovation that no other SDHC card can .
smart cards for authentication|enable smart card authentication