rfid tag tampering The researchers produced a light-powered antitampering tag that is about 4 square millimeters in size. They also demonstrated a machine-learning model that helps detect tampering by identifying similar glue pattern .
This project showcases how to exploit vulnerabilities in NFC cards using Arduino and RFID technology. By leveraging the MFRC522 RFID module, you can read and write data on NFC cards. The code provided offers a foundation for .Pro Credit Card Reader NFC v5.1.4 [Patched] APK [Latest] This app was made to read public data on an NFC banking card compliant with EMV norm. Pro version : • This .
0 · tamper proof tags
1 · tamper proof id
2 · tamper evident tags
3 · tamper evident rfid
4 · cryptographic tag
5 · anti tampering id tags
6 · anti tamper id
Each NFC tag type offers unique advantages depending on the application. While Type 1 and 2 .
Choosing the right RFID tagfor your application can be one of the more difficult parts involved with implementing a system because there are several factors like size, read range, attachment method, encasement, cost, etc. involved. Deciding which tag is the best fit can be even more complicated if the tag needs to meet . See more
Tampering– Tampering occurs when someone or something interferes with an item or product to cause damage or make unauthorized . See moreBesides the pharmaceutical industry, specifically over-the-counter medicine, tamper evident packaging is used in shipping high value equipment or sensitive documents, food and . See moreTo learn more about tamper evident RFID tags and their role in an item’s security, comment below or contact us! If you would like to learn more about all things RFID, check out our . See moreTamper evident packaging isn’t required to be uniquely identified with an RFID tag or barcode, but adding an RFID tag could increase the functionality of packaging and enable visibility into . See more
The researchers produced a light-powered antitampering tag that is about 4 square millimeters in size. They also demonstrated a machine-learning model that helps detect tampering by identifying similar glue pattern .
tamper proof tags
tamper proof id
Combining tamper evident packaging with product authentication methods can be accomplished using RFID tags. Currently deployed for high-end food and beverage products, like wine and spirits, RFID tags both provide item authentication and that . The researchers produced a light-powered antitampering tag that is about 4 square millimeters in size. They also demonstrated a machine-learning model that helps detect tampering by identifying similar glue pattern fingerprints with more than 99 percent accuracy.Whether you’re securing high-value goods or ensuring regulatory compliance, the right RFID tamper-evident label can provide peace of mind and safeguard your products from unauthorized access or tampering. In retail, tamper-evident RFID tags help prevent theft and tampering of high-value products. These tags are attached to each item and provide real-time inventory management, reduce shrinkage, and ensure product authenticity.
RFID tamper seals have emerged as a game-changing solution for securing high-value or sensitive assets like aircraft life vest storage containers, weapon racks, fire extinguishers and automatic emergency defibrillators (AEDs).RFID tamper evidence labels are suitable for anti-counterfeiting and product traceability of high-end ingredients and beverages. Examples include red wine, milk powder, cooking oil and other products that are susceptible to counterfeiting. A critical threat for RFID-based information systems is represented by data tampering, which corresponds to the malicious alteration of data recorded in the tag memory.
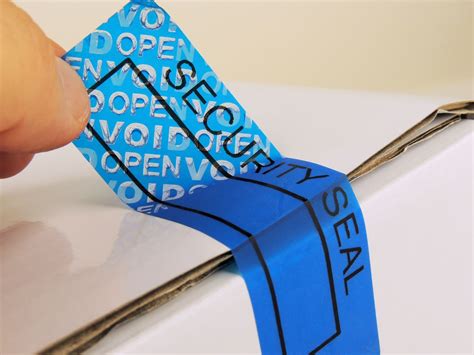
Introduces the characteristics and applications of RFID tamper-evident labels, and describes how to use such labels in commercial scenarios to prevent counterfeiting and verify authenticity.GAO’s tamper proof RFID tag is a type of radio-frequency identification tag designed to prevent unauthorized access or tampering. Unlike standard RFID tags, which can be easily removed or tampered with, tamper-proof RFID tags are built with additional security features to ensure that once attached, they cannot be removed or tampered with .
tamper evident tags
A tamper-proof RFID tag is a type of RFID tag that is designed to resist tampering or unauthorized removal. It is built with additional security features to prevent tampering attempts and ensure the integrity of the tag’s data. Combining tamper evident packaging with product authentication methods can be accomplished using RFID tags. Currently deployed for high-end food and beverage products, like wine and spirits, RFID tags both provide item authentication and that .
The researchers produced a light-powered antitampering tag that is about 4 square millimeters in size. They also demonstrated a machine-learning model that helps detect tampering by identifying similar glue pattern fingerprints with more than 99 percent accuracy.Whether you’re securing high-value goods or ensuring regulatory compliance, the right RFID tamper-evident label can provide peace of mind and safeguard your products from unauthorized access or tampering. In retail, tamper-evident RFID tags help prevent theft and tampering of high-value products. These tags are attached to each item and provide real-time inventory management, reduce shrinkage, and ensure product authenticity. RFID tamper seals have emerged as a game-changing solution for securing high-value or sensitive assets like aircraft life vest storage containers, weapon racks, fire extinguishers and automatic emergency defibrillators (AEDs).
read cal1card berkeley rfid github
RFID tamper evidence labels are suitable for anti-counterfeiting and product traceability of high-end ingredients and beverages. Examples include red wine, milk powder, cooking oil and other products that are susceptible to counterfeiting. A critical threat for RFID-based information systems is represented by data tampering, which corresponds to the malicious alteration of data recorded in the tag memory.Introduces the characteristics and applications of RFID tamper-evident labels, and describes how to use such labels in commercial scenarios to prevent counterfeiting and verify authenticity.GAO’s tamper proof RFID tag is a type of radio-frequency identification tag designed to prevent unauthorized access or tampering. Unlike standard RFID tags, which can be easily removed or tampered with, tamper-proof RFID tags are built with additional security features to ensure that once attached, they cannot be removed or tampered with .

tamper evident rfid
Join Date: Sep 2000. Location: Ottawa, Ontario, Canada. Programs: Aeroplan SE AND 1MM, .How do I use cardless access at Chase ATMs? Once at the ATM, open the mobile wallet on your phone and select your eligible Chase debit card. Eligible mobile wallets include Apple Pay and Samsung Pay. Tap your phone on the .
rfid tag tampering|cryptographic tag