rfid credit card cloning Once the hacker collects the information, the next step is to clone or spoof the captured cards. This creates a cloned card with an identical digital ID profile to the original, granting the hacker the same authorization and level of access. The National Football League playoffs for the 2021 season was the first time that the league featured a 17-game regular season schedule, and consequently the start of the playoffs was .
0 · rfid key fob copy
1 · rfid cloning tool
2 · rfid cloning software
3 · how to prevent rfid cloning
4 · how to duplicate rfid card
5 · how to copy rfid tag
6 · clone my key copy
7 · best rfid cloner
$15.00
rfid key fob copy
smart card windows 7 32 bit
rfid cloning tool
Cloning isn't necessary as the algorithm used for nfc with the emv cards is flawed, lacking a true rng. The predictable prns be used to negotiate transaction authentications. Another implementation flaw foils the 0/transaction cash limit by doing the transaction in a foreign .Each RFID chip has a unique serial number that cannot be changed, which identifies the chip . Cloning isn't necessary as the algorithm used for nfc with the emv cards is flawed, lacking a true rng. The predictable prns be used to negotiate transaction authentications. Another implementation flaw foils the 0/transaction cash limit by doing the transaction in .
Each RFID chip has a unique serial number that cannot be changed, which identifies the chip as unique. A serial number is then written to the tag’s memory. You could read the TID and serial number and make sure there was a correct match, in order to ensure the tag was not cloned. Once the hacker collects the information, the next step is to clone or spoof the captured cards. This creates a cloned card with an identical digital ID profile to the original, granting the hacker the same authorization and level of access. Can credit cards be cloned remotely with an RFID reader? This news story from "13 Investigates" shows Walt Augustinowicz (an RFID expert, and seller of RFID proof pouches) who has a portable reader than picks up credit card .

Tags which do not make use of password-protection or over-the-air (OTA) encryption can have their data banks copied into new tags. RFID tags (at least Class 1 Generation 2 tags, aka UHF RFID tags) are computationally active, not passive. Their "passive" nature refers to their not needing an attached power source. Uncover the risks and solutions around RFID cloning. Learn how to safeguard your access cards against unauthorized cloning. Secure your data today!
smart card wi fi
Criminals have established genius ways of copying cardholders’ data to make a clone RFID card. The clone RFID card is then used by criminals to access highly restricted areas or withdraw vast sums of money from the cardholder’s bank account. This article highlights various ways you can protect yourself from falling victim to RFID card . The easiest tutorial on how to copy or clone access cards (NFC or RFID). Which keycard or key fob copier is necessary? Learn how to proceed! We are here to support you if you need an advice on closing/opening a credit card, improving your credit scores, removing inaccurate information from your report, qualifying for a new card/mortgage/loan, investigating unknown information on your report and much more. Cloning is one of the most common security risks associated with RFID chips; it opens the door for credit card fraud and other physical infiltration. Recent advances in technology have made it easier for hackers to gain access to sensitive information stored on these chips, making them even more vulnerable than before.

Cloning isn't necessary as the algorithm used for nfc with the emv cards is flawed, lacking a true rng. The predictable prns be used to negotiate transaction authentications. Another implementation flaw foils the 0/transaction cash limit by doing the transaction in .Each RFID chip has a unique serial number that cannot be changed, which identifies the chip as unique. A serial number is then written to the tag’s memory. You could read the TID and serial number and make sure there was a correct match, in order to ensure the tag was not cloned. Once the hacker collects the information, the next step is to clone or spoof the captured cards. This creates a cloned card with an identical digital ID profile to the original, granting the hacker the same authorization and level of access.
Can credit cards be cloned remotely with an RFID reader? This news story from "13 Investigates" shows Walt Augustinowicz (an RFID expert, and seller of RFID proof pouches) who has a portable reader than picks up credit card .
Tags which do not make use of password-protection or over-the-air (OTA) encryption can have their data banks copied into new tags. RFID tags (at least Class 1 Generation 2 tags, aka UHF RFID tags) are computationally active, not passive. Their "passive" nature refers to their not needing an attached power source.
Uncover the risks and solutions around RFID cloning. Learn how to safeguard your access cards against unauthorized cloning. Secure your data today!
Criminals have established genius ways of copying cardholders’ data to make a clone RFID card. The clone RFID card is then used by criminals to access highly restricted areas or withdraw vast sums of money from the cardholder’s bank account. This article highlights various ways you can protect yourself from falling victim to RFID card .
The easiest tutorial on how to copy or clone access cards (NFC or RFID). Which keycard or key fob copier is necessary? Learn how to proceed! We are here to support you if you need an advice on closing/opening a credit card, improving your credit scores, removing inaccurate information from your report, qualifying for a new card/mortgage/loan, investigating unknown information on your report and much more.
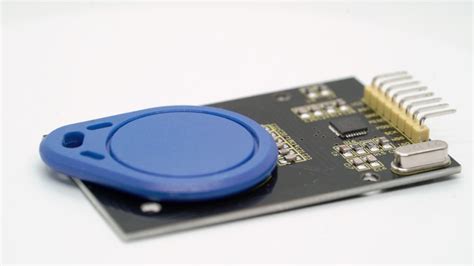
Ali Express is the cheapest you will find them. Gen4 is the best and it's gonna cost you about .
rfid credit card cloning|clone my key copy