security bit of tag rfid modification RFID Tag is used to tracking commodities and personal assets in the chain stores and even the human body and medical science. However, security and privacy problems have not yet been . Listen online to The Tiger 95.9 FM radio station 95.9 MHz FM for free – great choice for Auburn, United States. Listen live The Tiger 95.9 FM radio with Onlineradiobox.com . Tiger 95.9 WTGZ FM is the premiere alternative music .
0 · Top 10 RFID Security Concerns and Threats
1 · RFID Hacking: 6 Common RFID Attacks & 6 Ways to
2 · RFID Hacking: 6 Common RFID Attack
3 · Is it possible to provide security in Passi
4 · Investigating attacks to improve security and privacy in RFID
5 · Investigating attacks to improve securit
6 · Extensive fault emulation on RFID tags f
7 · An Enhanced Secure Authentication Sc
NFC. In addition to USB, the YubiKey 5 NFC keys also provide an NFC wireless interface for additional convenience. Unlike the YubiKey NEO, the YubiKey 5 NFC does not support RFID tags, such as MIFARE Classic and MIFARE DESFire.
RFID cards and tags can be rendered useless by hackers who generate a stronger signal than the RFID reader. This not only disrupts inventory tracking but also causes chaos by blocking access with ID cards.RFID Tag is used to tracking commodities and personal assets in the chain stores and even the human body and medical science. However, security and privacy problems have not yet been .
RFID cards and tags can be rendered useless by hackers who generate a stronger signal than the RFID reader. This not only disrupts inventory tracking but also causes chaos .
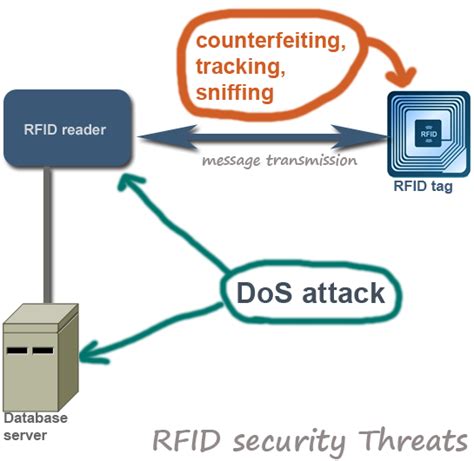
RFID Tag is used to tracking commodities and personal assets in the chain stores and even the human body and medical science. However, security and privacy problems have not yet been . Yes, it is quite possible to make passive tags secure, but the tag must have some local processing power, not just a static read-only memory that it reads out. The general .
The system is fully compatible with Ultra High Frequency (UHF) RFID systems without any modification. We implement a prototype of the system and conduct extensive experiments to . This paper proposes a method for evaluating the fault tolerance and security of RFID tags at the design level, by using an extensive random emulation of SBUs and MBUs .
Top 10 RFID Security Concerns and Threats
RFID tags are vulnerable to DoS/Desynchronization attacks because RFID tag and reader send out radio signals to each other in the open. Barcodes only reflect the beam of light .

ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ Select Download Format Security Bit Of Tag Rfid Modification Download . Examples include attacks employing unauthorized tag reading, modification of tag data, and attacks in the application middleware. Strategic layer includes all attacks that target .
Overview. Introduction to RFID and its applications. Types of security attacks to Passive RFID Tags. Impersonation. Information Leakage. Physical Manipulation. Types of .
Security and privacy issues of RFID tags can effect both organizations and individuals. Unprotected tags may be vulnerable to eavesdropping, traffic analysis, spoofing or .
RFID Hacking: 6 Common RFID Attacks & 6 Ways to
RFID cards and tags can be rendered useless by hackers who generate a stronger signal than the RFID reader. This not only disrupts inventory tracking but also causes chaos .
RFID Tag is used to tracking commodities and personal assets in the chain stores and even the human body and medical science. However, security and privacy problems have not yet been . Yes, it is quite possible to make passive tags secure, but the tag must have some local processing power, not just a static read-only memory that it reads out. The general .
The system is fully compatible with Ultra High Frequency (UHF) RFID systems without any modification. We implement a prototype of the system and conduct extensive experiments to . This paper proposes a method for evaluating the fault tolerance and security of RFID tags at the design level, by using an extensive random emulation of SBUs and MBUs .
RFID tags are vulnerable to DoS/Desynchronization attacks because RFID tag and reader send out radio signals to each other in the open. Barcodes only reflect the beam of light .ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ ᅠ Select Download Format Security Bit Of Tag Rfid Modification Download .
Examples include attacks employing unauthorized tag reading, modification of tag data, and attacks in the application middleware. Strategic layer includes all attacks that target . Overview. Introduction to RFID and its applications. Types of security attacks to Passive RFID Tags. Impersonation. Information Leakage. Physical Manipulation. Types of .
RFID Hacking: 6 Common RFID Attack

rfid based library management system documentation
rfid based attendance system using microcontroller
It is a card-size RFID NFC Reader Writer primarily designed as a professional tool .
security bit of tag rfid modification|RFID Hacking: 6 Common RFID Attack