smart card or usb token USB tokens work by storing digital certificates and encryption keys, which are used for secure authentication and encryption. When a user inserts the USB token into a computer, it prompts them to enter their password or biometric . To access this feature in the NFC Tools app you must navigate to the "Other" tab and click the .
0 · what is smart card number
1 · what is smart card authentication
2 · smart card identity
3 · smart card identification
4 · smart card based identification system
5 · smart card based authentication
6 · memory based smart card
7 · azure smart card authentication
DNFC and password protection. The NTAG216 chip has two sets of lock bytes. The first set are called the “static lock bytes” and are the last two bytes of page 02. The second set are called “dynamic lock bytes” and are the .

USB tokens work by storing digital certificates and encryption keys, which are used for secure authentication and encryption. When a user inserts the USB token into a computer, it prompts them to enter their password or biometric .If you have a Smart card or USB token for an ECA certificate, you will need to initiate an ECA Program Key recovery.USB tokens work by storing digital certificates and encryption keys, which are used for secure authentication and encryption. When a user inserts the USB token into a computer, it prompts them to enter their password or biometric data, and then it .
If you have a Smart card or USB token for an ECA certificate, you will need to initiate an ECA Program Key recovery.Smart card technology conforms to international standards (ISO/IEC 7816 and ISO/IEC 14443) and is available in a variety of form factors, including plastic cards, key fobs, watches, subscriber identification modules used in GSM mobile phones, and USB-based tokens.HID ® ActivID ® ActivClient ® is a smart card and a USB token middleware that allows enterprise and government customers to easily use the smart cards and the USB tokens to secure workstations and networks. Like the other YubiKey Series 5 devices, the 5C NFC does more than just MFA and password-less login; it can function as a Smart Card, store static passwords and Open PGP keys, and more.
Identity-Based Certificates: IdenTrust digital certificates stored on hardware (i.e. smart cards or USB tokens) provide the most secure solution for credentials that can be used with two-factor enabled applications. In order to use two-factor authentication, the application must .
what is smart card number
Control Access with Token-based Authentication. Two-factor authentication to networks using certificates stored on USB tokens or smart cards reduces the risk of breach compared to relying on passwords alone.USB Tokens and Smart Cards. A security token (or sometimes a hardware token, hard token, authentication token, USB token, cryptographic token, smart token, or key fob) may be a physical device that an authorized user of computer services is given to ease authentication.A Digital Signature Token or USB Token is a password-protected physical device used to establish personal identity. It enables users to access the network without a password.The USB security token is an equivalent of a reader-less smart card with advanced onboard cryptographic processor and physical tamper protected memory for personal information storage (such as private keys and digital certificates).
USB tokens work by storing digital certificates and encryption keys, which are used for secure authentication and encryption. When a user inserts the USB token into a computer, it prompts them to enter their password or biometric data, and then it .
what is smart card authentication
If you have a Smart card or USB token for an ECA certificate, you will need to initiate an ECA Program Key recovery.Smart card technology conforms to international standards (ISO/IEC 7816 and ISO/IEC 14443) and is available in a variety of form factors, including plastic cards, key fobs, watches, subscriber identification modules used in GSM mobile phones, and USB-based tokens.
HID ® ActivID ® ActivClient ® is a smart card and a USB token middleware that allows enterprise and government customers to easily use the smart cards and the USB tokens to secure workstations and networks.
Like the other YubiKey Series 5 devices, the 5C NFC does more than just MFA and password-less login; it can function as a Smart Card, store static passwords and Open PGP keys, and more.Identity-Based Certificates: IdenTrust digital certificates stored on hardware (i.e. smart cards or USB tokens) provide the most secure solution for credentials that can be used with two-factor enabled applications. In order to use two-factor authentication, the application must .
Control Access with Token-based Authentication. Two-factor authentication to networks using certificates stored on USB tokens or smart cards reduces the risk of breach compared to relying on passwords alone.USB Tokens and Smart Cards. A security token (or sometimes a hardware token, hard token, authentication token, USB token, cryptographic token, smart token, or key fob) may be a physical device that an authorized user of computer services is given to ease authentication.A Digital Signature Token or USB Token is a password-protected physical device used to establish personal identity. It enables users to access the network without a password.
rfid tags not working
rfid tags through sheet rock
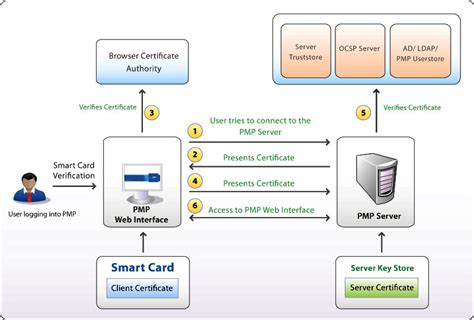
smart card identity
It means that your NFC (Near Field Communication) is turned on and your phone has come into contact with an NFC-enabled device or credit/debit card. If it is enabled, the NFC sensor will look for magnetic objects within its .
smart card or usb token|smart card based authentication