mutual authentication protocol for rfid system secure mutual authentication protocol for low-cost RFID systems, named as SMAP-LRS, to achieve higher security level and be compatible with the hardware restriction of passive RFID . NFC interactor is a powerful Near Field Communication tag reader / writer app, aimed at enthusiasts and developers. NFC Tag Reading and NDEF Parsing. Tap NFC tags to analyze their real contents. NFC interactor will instantly tell you .
0 · SDRLAP: A secure lightweight RFID mutual authentication
1 · RFID mutual authentication protocols
2 · Novel ECC
3 · Mutual authentication protocol for low cost passive tag in RFID
4 · Mutual Authentication Protocol for RFID System
5 · Mutual Authentication Protocol for RFID
6 · Mutual Authentication Protocol for Networked RFID Systems
7 · Mutual Authentication Protocol for Netw
8 · Hash
9 · Cloud
10 · A Secure Mutual Authentication Protocol for Low
11 · A Secure Mutual Authentication Protoco
12 · A Novel RFID Authentication Protocol Based on A Block
13 · A Lightweight RFID Mutual Authentication Protocol with PUF
14 · A Lightweight RFID Mutual Authenticatio
โค้ดแอปคลิปที่รวม NFC หรือแท็ก NFC: ถือ iPhone ไว้ใกล้กับแท็ก NFC. แผนที่: แตะลิงก์แอปคลิปบนบัตรข้อมูล (สำหรับตำแหน่งที่ตั้งที่รองรับ)
Authentication protocol, which is the process of verifying the claimed identity of a user, can be used between tag and reader as a way to mitigate security risks. In this paper, we study the RFID tag-reader mutual authentication scheme.We develop and present a RFID security protocol that allows mutual authentication between the reader and tag as well as secure communication of tag data. The protocol presented uses a .
secure mutual authentication protocol for low-cost RFID systems, named as SMAP-LRS, to achieve higher security level and be compatible with the hardware restriction of passive RFID .

In this work, we propose novel lightweight RFID mutual authentication protocols based on physically unclonable functions (PUFs), which is able to meet the security demands . Compared with most of the existing RFID authentication protocols with the traditional key updating mechanism, SDRLAP guarantees the security and privacy of RFID .
It offers mutual authentication and data integrity that has become highly employed in RFID applications. In this paper, we present a novel secure ECC-based RFID authentication . For instance, in RFID enabled smart healthcare systems, improper authentication protocols may result in the failure to provide accurate information promptly, . Firstly, two .
SDRLAP: A secure lightweight RFID mutual authentication
Several protocols have been proposed to resolve security and privacy issues in RFID systems. However, the earlier suggested algorithms do not satisfy all of the security requirements. In .
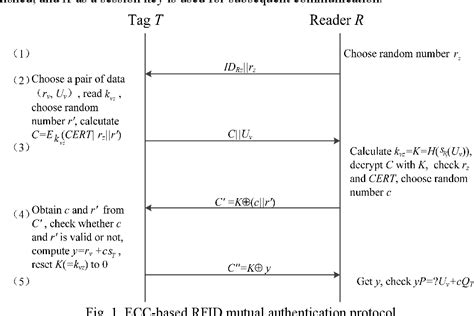
A secure and stable RFID authentication scheme is critical to IoT. This paper puts forward an efficient and reliable cloud-based RFID authentication scheme. In order to reduce .Authentication protocol, which is the process of verifying the claimed identity of a user, can be used between tag and reader as a way to mitigate security risks. In this paper, we study the RFID tag-reader mutual authentication scheme.
We develop and present a RFID security protocol that allows mutual authentication between the reader and tag as well as secure communication of tag data. The protocol presented uses a hybrid method to provide strong security while ensuring the resource requirements are low.
secure mutual authentication protocol for low-cost RFID systems, named as SMAP-LRS, to achieve higher security level and be compatible with the hardware restriction of passive RFID tag at the same time.
RFID mutual authentication protocols
In this work, we propose novel lightweight RFID mutual authentication protocols based on physically unclonable functions (PUFs), which is able to meet the security demands of RFID system and satisfy the hardware limitation of low-cost tags.
This paper creates a new ultra-lightweight authentication scheme for RFID. This scheme comprises of three different phases: tag identification phase, mutual authentication phase, and pseudonyms and key updating phase. This scheme uses Rot operation, “MIX” function, and XOR operation to computes mutual authentication. Compared with most of the existing RFID authentication protocols with the traditional key updating mechanism, SDRLAP guarantees the security and privacy of RFID systems, and meanwhile has the obvious advantages in terms of computational cost, storage requirement and communication overhead.
It offers mutual authentication and data integrity that has become highly employed in RFID applications. In this paper, we present a novel secure ECC-based RFID authentication protocol that meets the security needs of existing published . For instance, in RFID enabled smart healthcare systems, improper authentication protocols may result in the failure to provide accurate information promptly, . Firstly, two lightweight RFID mutual authentication schemes for IoT environment were shown in . These protocols utilized a hash function and a random number (RN) generator for secure .
Several protocols have been proposed to resolve security and privacy issues in RFID systems. However, the earlier suggested algorithms do not satisfy all of the security requirements. In this paper we introduce our hash-based mutual authentication protocol which meets all . A secure and stable RFID authentication scheme is critical to IoT. This paper puts forward an efficient and reliable cloud-based RFID authentication scheme. In order to reduce the RFID tag's overhead, the proposed authentication scheme explores the rotation and enhanced permutation to encrypt data. The proposed protocol not only resists the .
Authentication protocol, which is the process of verifying the claimed identity of a user, can be used between tag and reader as a way to mitigate security risks. In this paper, we study the RFID tag-reader mutual authentication scheme.We develop and present a RFID security protocol that allows mutual authentication between the reader and tag as well as secure communication of tag data. The protocol presented uses a hybrid method to provide strong security while ensuring the resource requirements are low.secure mutual authentication protocol for low-cost RFID systems, named as SMAP-LRS, to achieve higher security level and be compatible with the hardware restriction of passive RFID tag at the same time. In this work, we propose novel lightweight RFID mutual authentication protocols based on physically unclonable functions (PUFs), which is able to meet the security demands of RFID system and satisfy the hardware limitation of low-cost tags.
Novel ECC
This paper creates a new ultra-lightweight authentication scheme for RFID. This scheme comprises of three different phases: tag identification phase, mutual authentication phase, and pseudonyms and key updating phase. This scheme uses Rot operation, “MIX” function, and XOR operation to computes mutual authentication. Compared with most of the existing RFID authentication protocols with the traditional key updating mechanism, SDRLAP guarantees the security and privacy of RFID systems, and meanwhile has the obvious advantages in terms of computational cost, storage requirement and communication overhead.

It offers mutual authentication and data integrity that has become highly employed in RFID applications. In this paper, we present a novel secure ECC-based RFID authentication protocol that meets the security needs of existing published . For instance, in RFID enabled smart healthcare systems, improper authentication protocols may result in the failure to provide accurate information promptly, . Firstly, two lightweight RFID mutual authentication schemes for IoT environment were shown in . These protocols utilized a hash function and a random number (RN) generator for secure .Several protocols have been proposed to resolve security and privacy issues in RFID systems. However, the earlier suggested algorithms do not satisfy all of the security requirements. In this paper we introduce our hash-based mutual authentication protocol which meets all .
how to know the smart card number
how to program smart card
We use aliexpress affiliate links for the components and the tools. Some Ad-blockers might block these links and thus they seem to appear . See more
mutual authentication protocol for rfid system|A Secure Mutual Authentication Protoco